Microsoft Exchange Servers with flaws across the globe are hit by yet another ransomware termed Cuba ransomware.
The ransomware gang is exploiting the Exchange Server vulnerabilities, including ProxyLogon and ProxyShell, to gain initial access to the organizations’ network and encrypt the connected devices for a ransom.
Cuba Ransomware History
Cuba ransomware operation started in late 2019. Initially slow, ransomware picked up the pace in 2020 and 2021. FBI had issued an advisory on Cuba ransomware back in December 2021 after 49 U.S. based organizations in at least five critical infrastructure sectors, such as IT, manufacturing, financial, government, and healthcare were compromised.
According to the FBI, the threat actors behind the attacks have demanded $74 million and received at least $43+ million in ransom payments from their victims.
Mandiant tracks (a cyber-security firm) has codenamed the gang as UNC2596—known for leaking stolen data on the groups’ shaming websites (sites where threat actors publish or sell stolen data), and the Cuba ransomware as COLDDRAW.
The report by Mandiant tracks shows that the gang is primarily targeting critical organizations based in the United States and Canada, followed by Australia, Austria, Belgium, Columbia, Germany, India, Jordon, Poland, and the United Kingdom.
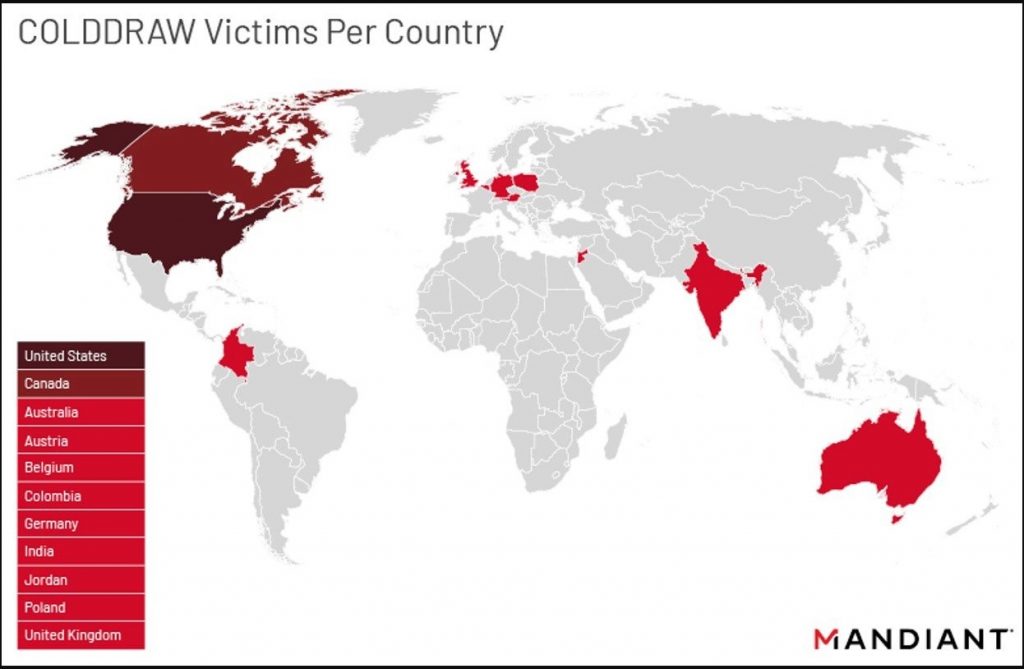 Image Source – Mandiant
Image Source – Mandiant How is Cuba Ransomware Gang Compromising the Exchange Server?
The Cuba ransomware is distributed via a loader called Hancitor malware—used for dropping and executing stealers, such as publically available NetSupport Remote Access Trojans or RATs, BUGHATCH, and create backdoors for persistent access and lateral movements in the targeted organizations’ network.
The gang uses phishing emails to target Exchange Servers flaws, compromised user credentials, or Remote Desktop Protocol (RDP) tools to gain initial access. After gaining the initial access, the ransomware installs the CobaltStrike beacon via PowerShell on the victim’s network. Upon installation, the ransomware downloads pones.exe for password acquisition and krots.exe to enable Cuba ransomware to write to compromised systems’ temporary files (TMP).
Once the TMP file is uploaded, the korts.exe is deleted, and the TMP file, including the API calls related to memory injection executed on the compromised network. After TMP file execution, the file is deleted, and the compromised system starts communicating with the malware repository.
Sample Cuba Note,
Good day. All your files are encrypted. For decryption, contact us.
Write here iracomp3@protonmail.com
We also inform you that we downloaded your databases, FTP server, and file server to our servers.
* Do not rename encrypted files
* Do not try to decrypt your data using third party software,
it may cause permanent data loss.
How to Protect Exchange Servers from Cuba Ransomware?
To protect Exchange Servers against Cuba and other ransomware or malicious attacks, follow these FBI recommendations.
Besides, patch the server immediately with the latest Security and Cumulative Updates available for your Exchange Server version.
Follow these steps to check the server’s health and identify vulnerabilities you need to patch.
Step 1: Run HealthChecker Script
Use HealthChecker.ps1 PowerShell script released by Microsoft to check the Exchange Server health. The script currently supports Microsoft Exchange Server 2013, 2016, and 2019.
The steps are as follows,
- Download the HealthChecker.ps1 PowerShell script on your server or system connected to the domain.
- Launch Exchange Management Shell (EMS), PowerShell, or Command Prompt as administrator and use the cd command to navigate to the folder location where HealthChecker.ps1 script is downloaded. For instance,
cd C:\Users\ProfileName\Downloads\
- Then execute the HealtHChecker script on your Exchange Server by running the following command in the EMS, PowerShell, or Command Prompt window.
.\HealthChecker.ps1
- To generate a detailed HTML report on the Exchange Server health status, run the following command.
.\HealthChecker.ps1 -BuildHtmlServersReport
If you receive a warning or error message while running the script, run the following command to bypass the execution policy and execute the HealthChecker.ps1 script.
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
The HTML report is generated and stored at the same location where the ‘HealthChecker’ script is present. Open the HTML file in any browser to check the server health and patch the vulnerabilities, if any, by following the next step.
Step 2: Download and Install Exchange Server Updates
If the HTML report detects health issues or vulnerabilities, use the links to download the updates and install them. Please note that the latest security updates are available only for the following Exchange Server CUs.
- Exchange Server 2013 CU23
- Exchange Server 2016 CU21 and CU22
- Exchange Server 2019 CU10 and CU11
Refer to our detailed guide to download and install Cumulative and Security updates on Exchange Server.
You can also follow our blog Microsoft Exchange Remote Code Execution Vulnerability Flaws and Their Fixes to stay updated about the newer Exchange Server threats, vulnerabilities, and updates.
Conclusion
To stay protected from ransomware attacks, organizations need to strengthen their security parameters and, most importantly, update the server as soon as possible. Ransomware gangs, such as UNC2596, often target vulnerable Exchange Servers as they are easy to compromise and gain access to.
However, if the server has been compromised or the database has been damaged due to the malicious attack, it is recommended that you set up a new identical server and restore mailboxes to the new server from your backup. If a backup isn’t available or obsolete, you can use Exchange recovery software, such as Stellar Repair for Exchange, to repair the damaged databases in your compromised server, recover mailboxes and export them directly to your new Live Exchange Server or Office 365.