As hard drives store much of your private data, many people turn to encryption to safeguard them against unauthorized access. Two of the most common ways to protect your data using encryption are: A full-disk encryption which locks all the system files and personal data and a file-level encryption that only locks specific files, folders, or partitions instead of the complete drive.
Many commercial encryption applications are already in use. On Windows, Microsoft’s BitLocker comes preinstalled, while free and open-source examples include VeraCrypt, DiskCryptor. These are just a few example that can ensure that your drive is encrypted to your desired degree of safety. However, sometimes the bulletproof level of protection can backfire.
You know what I’m talking about, when the very system designed to keep others out also locks you out of your own data. That’s when you realize that you’ve got a problem on your hands.
Encrypted Storage Drives: Why Do You Need Them
The main deal about encrypted storage drives is that they serve as a full-proof safety mechanism against unauthorized access.
Protects from theft/lost device: Let’s say you are at a coffee shop and your laptop gets wiped with a stranger’s. Without encryption, whoever took it can access everything – your photos, videos, documents, and files containing other important data.
Prevents identity theft: Someone stealing your private information like ID cards, addresses, Social Security numbers, and bank accounts can be your worst nightmare, but encryption keeps you covered.
Protects proprietary data: If someone is an employer or a businessperson with sensitive and proprietary information or client information, they wouldn’t want their competitors getting their hands on such files.
Easy disposal of devices: When the time comes to get rid of an old machine through resale or recycling, encryption can allow for easy data wipe of what once was.
Encrypted Storage Drives: The Basics of How it Works
The encrypted drive keeps all files concealed by using encryption applications that transform the files into unreadable data. Only with a password punch can the encryption be undone.
Those without permissions see dynamic strings of letters and symbols. Yet, when an approved individual opens a file on the drive with decrypted access, the drive seamlessly performs the reversal through its application layer back to readable file format.
Encrypted drives generally fall into two categories, each with its own way of handling the lock-and-key process.
Hardware-based Encryption
In this approach, the encryption is integrated inside the drive’s own circuitry, often in the controller chip or firmware. Every read or write operation is encrypted or decrypted instantly, without the user having to perform anything manually. This happens because the keys never leave the device which reduces the risk from software-level attacks, such as malware, making it a popular option for environments where security hardware needs to be tightly controlled.
Software-based Encryption
Software encryption works differently from what we’ve considered so far. It runs on the host and does all the encrypting/decrypting for you. Thus, to access the drive, the user must input a password or passphrase. Software encryption works across many types of devices and operating systems. Its versatility means of encryption making it flexible for those who move data from device to device.
However, this flexibility makes it less secure if the system is compromised by malware. This is because the keys are managed in memory/software rather than sealed inside a hardware.
Encrypted Storage Drive: What’s Causing Data Loss
File deletion: An encrypted chunk of information (a file, folder, or volume) can be removed by the user or an application either intentionally or unintentionally. This applies to encrypted container files created by software such as VeraCrypt or DiskCryptor. In most such cases, the deleted data can be restored by a recovery software, if it hasn’t already been overwritten.
Possible actions:
- Restore from a backup
- Run data recovery software
Lost certificate: Often central to encryption systems, certificates or key files are very helpful in unlocking the data. Without them, the information remains pretty useless as it remains scrambled and unreadable. It becomes nearly impossible to make any kind of recovery in case the certificate is gone and there are no existing backups. Even if the raw data is somehow retrievable, it will still be locked and inaccessible.
Note: Recovery using certificates is applicable only in case of Windows EFS (Encrypting File System), not for BitLocker or third-party encryptions.
Possible actions:
- Search for the missing certificate
- Restore from a backup
Accidental formatting: Formatting an encrypted drive can be especially damaging. Reformatting it using the same file system makes standard recovery methods ineffective as the original file system records are overwritten. It also renders signature-based scans useless as the encrypted content doesn’t find recognizable file patterns to match anymore, making recovery nearly impossible without backups or saved headers.
Possible actions:
- Restore from a backup
- Run data recovery software
Ransomware attack: Ransomware hijacks a system and encrypts the data within. The attacker demands payment (often in cryptocurrency) in exchange for a decryption key. Even if you pay for ransom, they may not provide you with one, and might not even release your system back to you in better condition.
Possible actions:
- Try a reputable decryption tool
- Restore from a backup
Encrypted Data Recovery: The Methods
Data recovery is often an unpredictable process, and recovering encrypted data even more so. The methods below have worked in the past, hopefully they may work for you as well.Before trying to recover, do not writing any new data to the drive and create an image of the drive first.
Note for SSD users: SSDs use the TRIM command which can permanently delete data and make recovery impossible. If your encrypted SSD holds valuable data, disable TRIM to improve the likelihood of recovery.
Method 1: Restore Files from Backup
Worried about losing encrypted file? You’ve probably heard this before but nothing beats having a backup in place. Whether you’re going to restore a single document or a whole system, it’s a cake walk. But if the backup does not exist, skip ahead to the next option.
The steps vary from user to user depending on the backup tool used. Here’s how to restore files using a File History backup in Windows:
- Open the Start menu, type File History, and launch it.
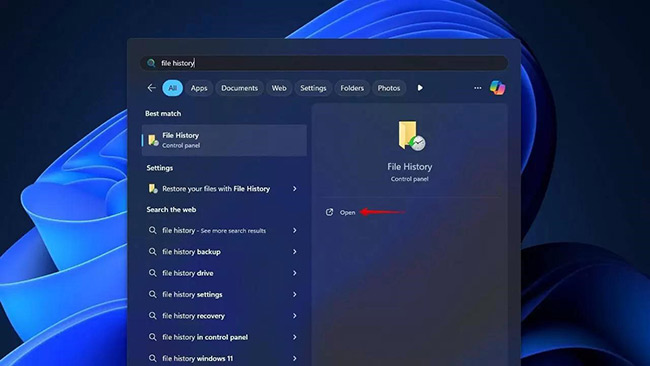
- Select Restore personal files.
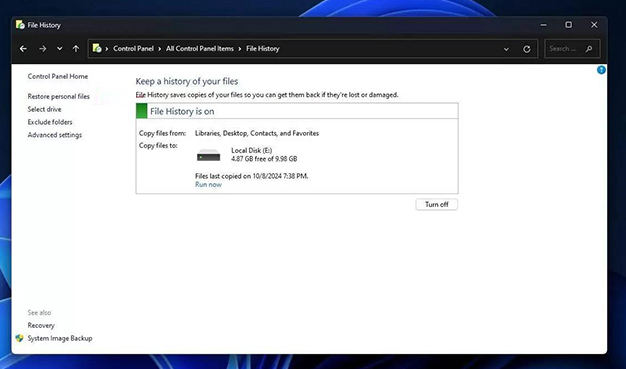
- Browse to the items from your encrypted drive that you want to recover.
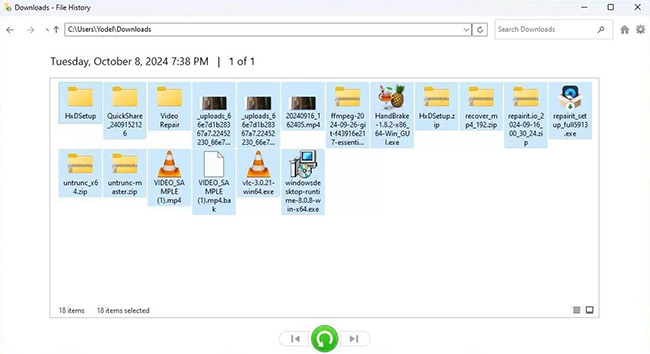
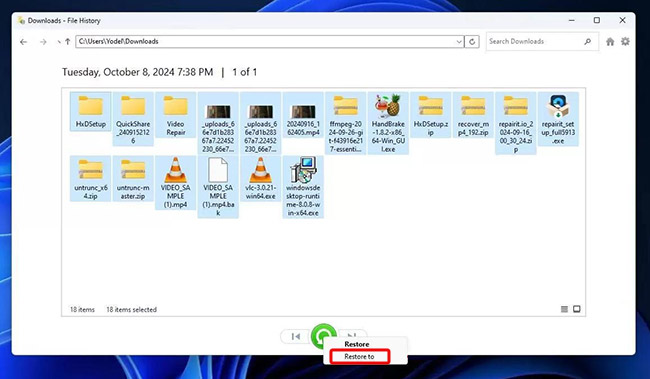
- Right-click the green Restore button and choose Restore to pick a location.
Method 2: Recover Using Data Recovery Software
Encrypted data can only be recovered under two conditions:
- You have the right credentials (passkey).
- The file system is not damaged.
Encrypted content is scrambled into patterns that reveal nothing about the original data. The only practical way to find and restore it is to use the Windows File system’s own records.
If you have decrypted the hard drive using the above methods but still cannot locate your files, it’s possible that your data has become corrupted. In this scenario, we recommend using a Windows data recovery software – Stellar Data Recovery Standard. The software helps you recover data lost due to logical corruption, accidental deletion, formatting, and other issues.
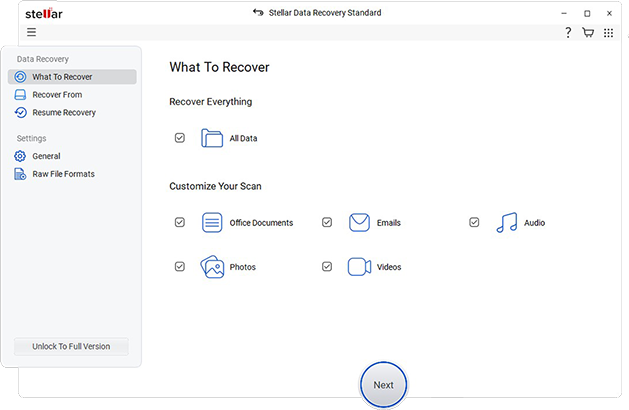
Method 3: Recover Using Recovery Key Backup
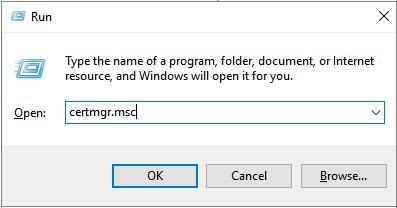
Certificate Manager is an in-built utility tool in Windows which can be used to unlock data from an encrypted storage drive that uses Encrypting File System (EFS) for encryption. All you got to do is to import the EFS encryption key to a designated location and use it to decrypt the drive.
- To use this utility tool, press Win + R. This will launch the Run dialog box. Then type certmgr.msc and press Enter.
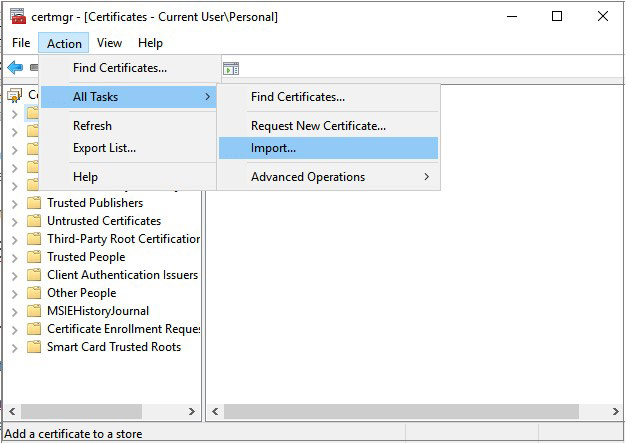
- Under the various categories of Certificates, right-click on Personal and select Import from the All Tasks menu.
- A certificate import wizard will pop up and guide you through selecting the certificate file from your storage. Follow the prompts to confirm the details and approve the import to the preferred location.
- After completion, use the key to decrypt your files.
Note: For BitLocker encrypted drives, if you have backed up your BitLocker Recovery key to your Microsoft account, it can be recovered from there.
Bottom Line
In order to keep information locked away, encryption is designed to be heavily secure from anyone without the right certificate, key, or login details. This also means recovery becomes extremely difficult if any of these are missing.
With proper access, however, it’s still possible to bring back encrypted files that were deleted. Planning ahead is most likely to work here as it is the most effective way to avoid losing them in the first place. That is why it is important to take the time to set up a reliable backup routine to ensure that your data is safely stored somewhere but can easily accessed in time of need.