Researchers at Microsoft Threat intelligence Center (MSTIC) revealed at least six threat actors from West Asian countries—Iran deploying web shells and ransomware for extortion and sabotaging their victims.
Cybersecurity agencies based in the United States, United Kingdom, and Australia have also issued a joint advisory on the ongoing wave of attacks carried out by state-sponsored threat groups found exploiting the Microsoft Exchange ProxyShell and Fortinet vulnerabilities. The threat actors are actively scanning devices on ports 4443, 8443, and 10443 for following FortiOS vulnerabilities,
- CVE-2018-13379
- CVE-2019-5591
- CVE-2020-12812 (enumerated devices)
The vulnerabilities allow the threat actors to gather text credentials from the session file. It is estimated that threat actors have collected credentials from over 900 Fortinet VPN servers in Europe, the United States, and Israel.
The threat actors are also exploiting the ProxyShell vulnerabilities (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) to compromise the network and deploy ransomware.
According to MSTIC, the Iranian attackers are increasingly capable, more patient, and persistent with their social engineering campaigns carrying out aggressive brute force attacks in waves of six to eight weeks on average.
Microsoft has provided detailed information on the timeline of ransomware attacks by Iranian APTs that started back in September 2020.
In another incident, Mandiant researchers found threat actors exploiting the ProxyShell and ProxyLogon vulnerabilities (patched earlier this year) and dropping the web shells in a different way than used earlier—making them difficult to detect.
In some cases, instead of dropping web shells, the threat actors created their hidden privileged mailboxes that can be used to take over other accounts.
How Are Attackers Deploying Ransomware on Vulnerable Exchange Servers?
After compromising the Exchange Server by exploiting the ProxyShell and ProxyLogon vulnerabilities, the threat actors distribute the malicious email to the company’s users using the compromised Exchange Server. The attackers reply to the company’s emails in reply-chain attack to send malicious attachments.
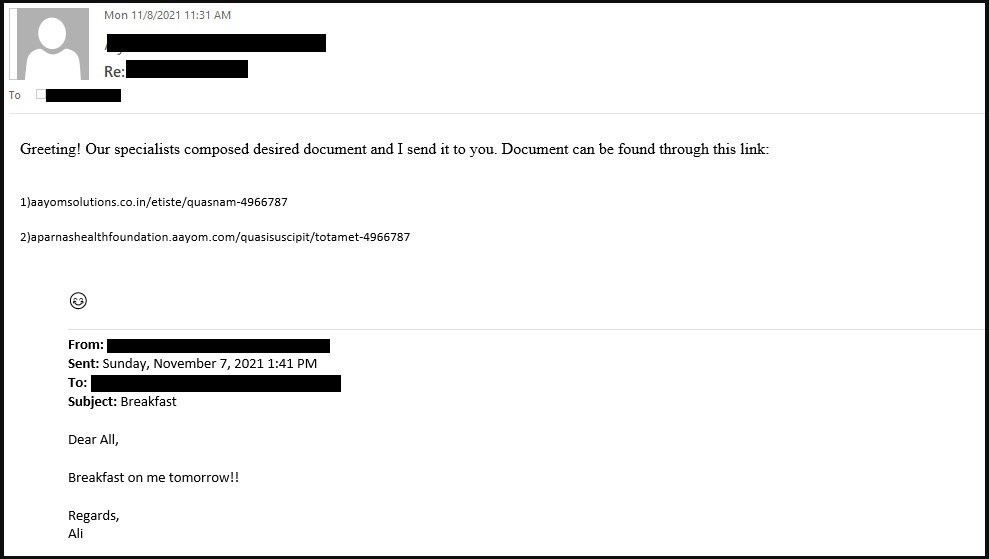
The email appears to be a continuation of previous emails or discussions between the employees that leads to trusting the email as a legitimate one and tricking the users in the organization to open the malicious attachment.
The downloaded attachments linked in emails are Microsoft Excel templates that ask recipients to ‘Enable Editing’. However, once the Excel sheet is enabled for editing, malicious macros download and install malware, such as Qbot, SquirrelWaffle, Cobalt Strike, etc.
This reply-chain attack bypasses the email protection system and does not raise any alarm, making it effective against human recipients.
Steps to Safeguard Your Organization from These Attacks
According to Shodan, more than 25000 Exchange Servers are still unpatched and vulnerable to ProxyShell attacks.
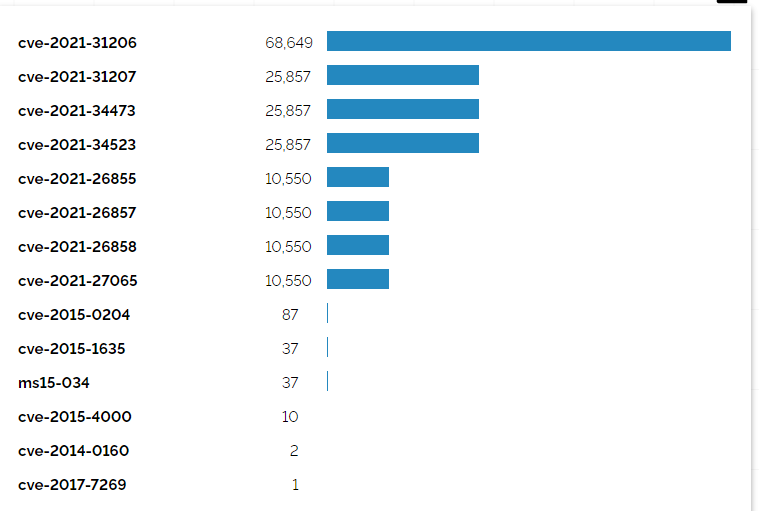
However, the real number of unpatched servers is estimated to be much higher.
Organizations with unpatched internet-facing Exchange Servers are at significant risk. However, Organizations with patched servers also need to strengthen their security and review their Exchange Servers for unknown files or suspicious activities on the server, mailbox permissions, and accounts.
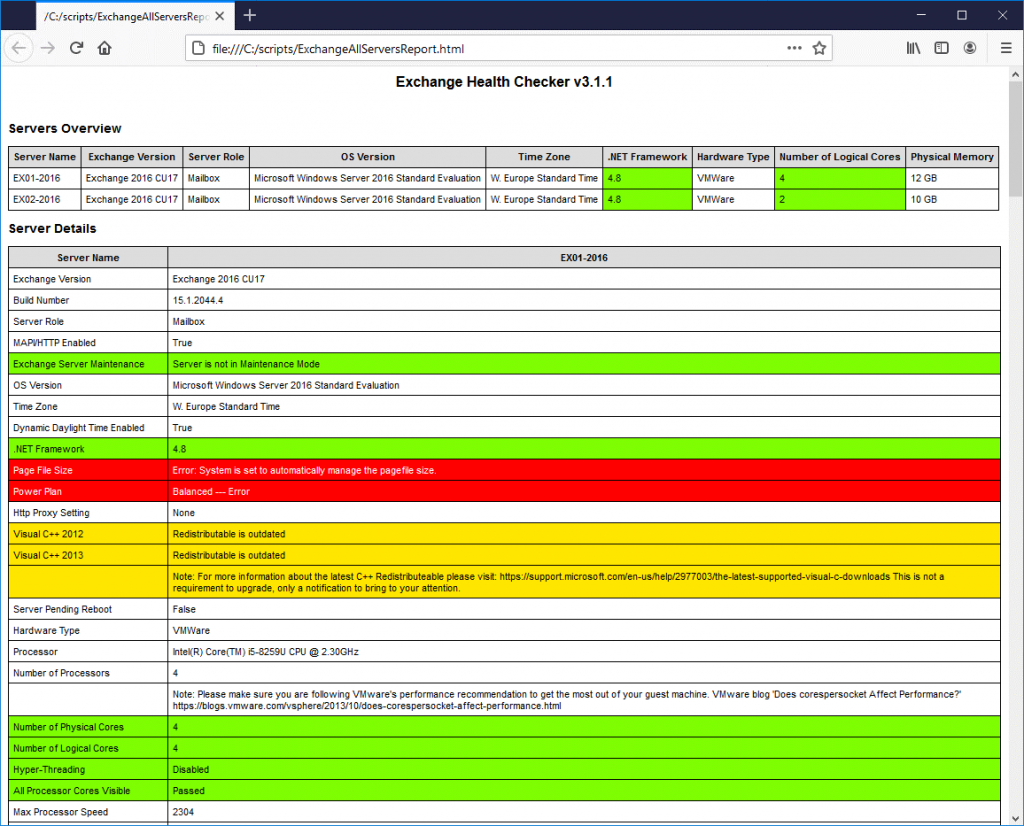
Step 1: Run HealthChecker Script
Download and run HealthChecker.ps1 PowerShell script to check the server health, performance, and configuration issues. You can generate a detailed report in an HTML file by using the following command,
.\HealthChecker.ps1 –BuildHtmlServersReport
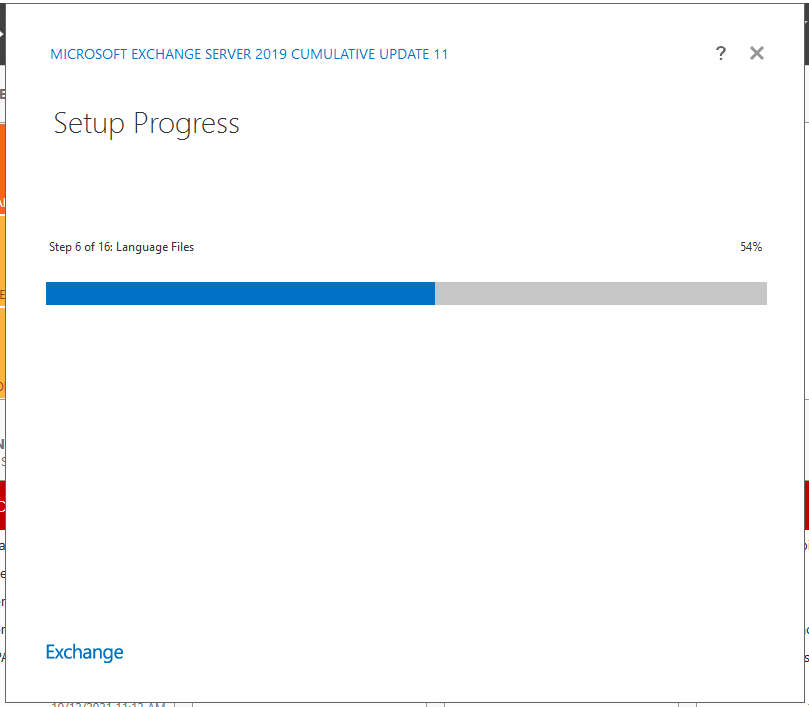
Step 2: Update Server
To protect your organization from malicious attacks, update the Exchange Server to the latest Cumulative Update and apply the November 2021 Security Updates to patch ProxyShell vulnerabilities. Use the Exchange Deployment Assistant to learn steps to update and patch your Exchange Server with the latest CUs and protect against malicious attacks.
Step 3: Strengthen Server Security
After update, review and fortify server security measures. Also, apply following mitigations to reduce the risk.
- Check and update the Allow List and Block List to allow/block URLs, files, domains, etc.
- If your organization is not using FortiOS, add the key artifact used by FortiOS to your organization’s block list and prevent any attempt to install or run this program or associated files.
- Implement a disaster recovery plan and backup regularly.
- Enforce strict password policy—Change password after a certain duration and prevent password reuse.
- Require administrator privilege to install software.
- Implement 2-Factor or multifactor authentication.
- Review and audit users with admin privileges.
- Do not use Public networks or Wi-Fi and use VPN for secure access.
- Aware and train users in your organization to recognize and avoid phishing emails.
Conclusion
Threat actors are actively scanning vulnerable Exchange Servers and exploiting the ProxyShell vulnerabilities to compromise unpatched Exchange Server and deploy ransomware or install web shells for backdoors and future attacks. Keeping the server unpatched is an open invitation to threat actors. We urge our readers to patch their servers and strengthen server security as soon as possible to stay protected against these threats.
However, in an unfortunate incident, if your server is compromised or crashed after the malicious attack, set up a new Exchange server. Never use the compromised server even if it’s fixed, as it may have web shells that attackers may use for future attacks.
Use the backup to restore mailboxes on the new server or an Exchange recovery software, such as Stellar Repair for Exchange, if the backup isn’t available. The software helps you recover mailboxes from the database on a compromised Exchange Server, even if the database is inaccessible or corrupt, and restores them to your new Exchange Server or Office 365 tenant directly in a few clicks.