Ransomware is a type of cyber attack, where the attacker locks a user's computer or data using encryption, and demands a ransom to decrypt the data and restore access. Given this modus operandi of ransomware, cyberattackers tend to attack organizations' databases, as they are likely to contain sensitive information like customers' personal data, employee information, and more. It's estimated that there were 1,386 victims of ransomware attacks in the second quarter of 2023 alone, a huge jump from 831 in Q1 of 2023. Also, the United Nations estimates that by 2031, a ransomware attack can happen every two seconds, causing the world $265 billion yearly. Given this growing threat, organizations must take measures to safeguard their databases from potential ransomware attacks.
To help organizations navigate this tricky space, in this article series, we talk about the different ransomware families, the common vectors to watch out for, and prevention and mitigation strategies that can protect databases from these cyber criminals.
Understanding Ransomware and Its Impact on Databases
Ransomware is a virus that's transmitted commonly through social engineering attacks. It often spreads through malicious email attachments, as downloads from compromised websites and apps, and even from infected external devices that connect to an organization's network.
How Does a Ransomware Work?
When a user downloads a malicious attachment, visits a compromised website, or connects an infected device, the malware spreads quickly to the organization's network. Sometimes, advanced ransomware programs can directly find loopholes in an organization's network, and enter through this vulnerability to attack the database.
Once the malware enters an organization's network, it finds its way to the database to encrypt it. After the database is fully encrypted, the ransomware displays a message that the database is compromised and provides detailed instructions on remediation. Due to the anonymity of bitcoins, most ransomware attackers demand the organization to pay a certain amount, often in millions, to a Bitcoin account. Once the transfer is done, the attacker provides the decryption key, using which the organization can restore its content. In most cases, the attackers don't steal the data, provided the organization pays the demanded ransom. That said, there's no guarantee that the attackers will restore access, even after the ransom is paid.
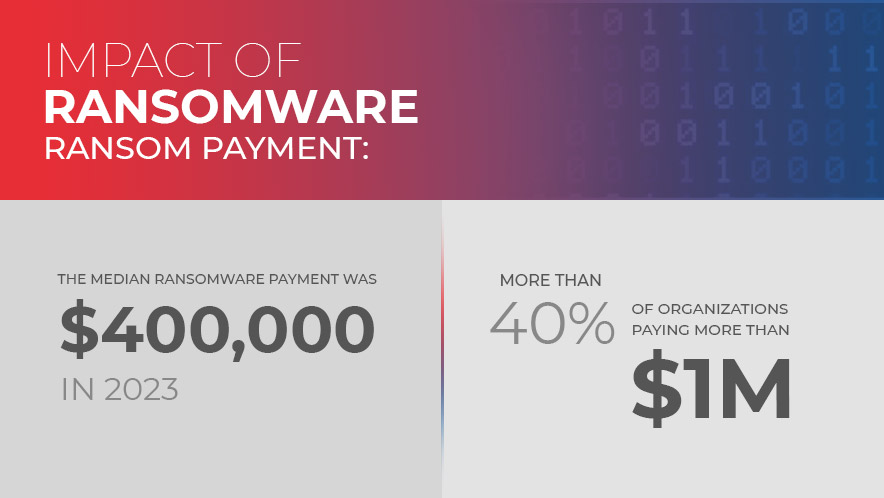
Impact of Ransomware

Ransomware attacks are hard to detect and can impact all types of databases, including Exchange databases, SQL databases, Access databases, and others. Such attacks also lead to extensive data loss, which in turn, has profound financial and operational implications for organizations.
- Ransom payment: The median ransomware payment was $400,000 in 2023, with more than 40% of organizations paying more than $1 million in ransom.
- Productivity loss: The average downtime after a ransomware attack was 22 days.
- Business targets: Due to financial and productivity loss, organizations often struggle to meet their SLAs and commitments to their clients, leading to a loss of trust.
- Reputational damage: An organization that's attacked by ransomware is often perceived as insecure and untrustworthy.
- Financial loss: When all aspects are put together, the loss is an average of $1.85 million for every attack.
- Data loss: Some ransomware attacks can lead to a permanent loss of data and files, especially if the decryption process was not done properly.
- Compliance issues: Data loss and damage to sensitive data can hinder an organization's ability to meet compliance requirements.
- Employee morale: When employees are unable to access the data they want, it can impact their work, and in turn, their morale.
To avoid such costly implications, organizations must take measures to protect from a ransomware attack, and the first step towards that can be to better understand different ransomware families and their modus operandi.
An Overview of Ransomware Families
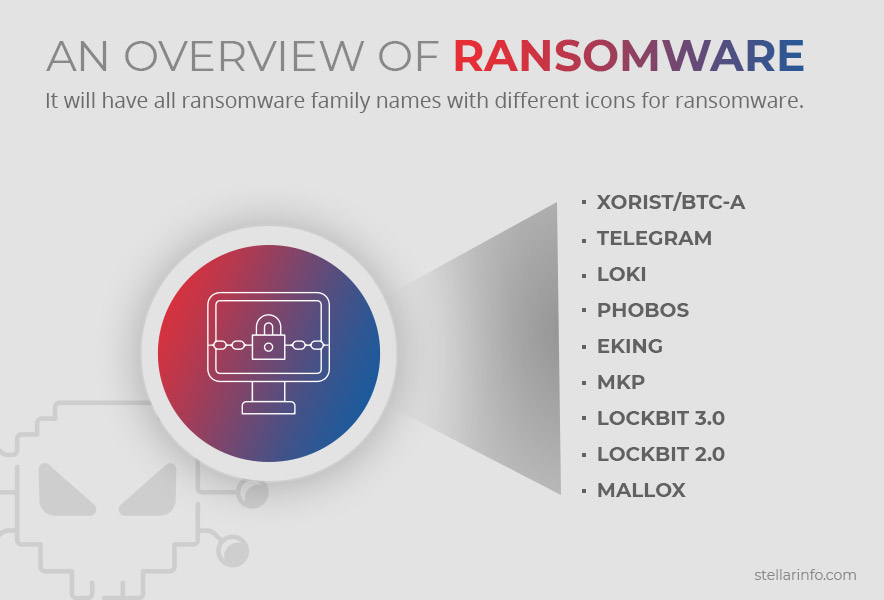
No ransomware attack is a random occurrence, rather they are a planned attack on organizations. This means they follow a specific style and pattern. Ransomware attacks are grouped into different families based on their style, code signatures, common malicious commands, and viral payloads. This pattern is also attributed to the fact that there are only a certain number of ransomware programs created in this world, and they are spread through affiliate programs. By grouping the attack into a family, you can better understand how it works, and what measures you must take to protect your organization.
Below are some of the prominent ransomware families.
Ransomware Family: Xorist/BTC-A
The Xorist family of ransomware secretly infiltrates systems, encrypts every file stored on the device, and adds one of the following extensions to each file:
be_deleted_this_is_not_a_joke, NEED-TO-MAKE-PAYMENT-OR-ALL-YOUR-FILLES-WILL-BE-DELETED-CRITICAL-SITUATION-URGENT-ATTENTION-24-HOURS-TO-PAY-OR-EVERYTHING-WILL-BE-PERMANENTLY-DELETED-FOREVER, .mbrcodes, ...DATA_IS_SAFE_YOU_NEED_TO_MAKE_THE_PAYMENT_IN_MAXIM_24_HOURS_OR_
ALL_YOUR_IMPORTANT_FILES_WILL_BE_LOST_FOREVER_PLEASE_BE_REZONABLE_IS_NOT_
A_JOKE_TIME_IS_LIMITED, PrOtOnIs, Files-Frozen-NEED-TO-MAKE-PAYMENT-FOR-DECRYPTOR-OR-ALL-YOUR-FILES-WILL-BE-PERMANENLTY-DELETE, .cryptedx, CerBerSysLocked0009881, error77002017111, Blocked2, TaRoNiS, Cerber_RansomWare@qq.com, .hello, .brb, RusVon, fast_decrypt_and_protect@tutanota.com, .xdata,SaMsUnG, .zixer2, .antihacker2017, .error, .errorfiles, .@EnCrYpTeD2016@, .pa2384259, .encoderpass, .fileiscryptedhard, .6FKR8d, .EnCiPhErEd, .73i87A, .p5tkjw, .PoAr2w, .xwz, .ava or .DECRYPT-ID-[victim's_ID].
It is distributed through email attachments, torrent downloads, and malicious ads.
After encrypting the files, this program creates a "How to Decrypt.txt" file on the system's desktop. The victim has to communicate through a text message in a specific pattern to a phone number, and only a certain number of text messages are allowed. This ransomware uses the Encoder Builder tool available on the dark web.
Ransomware Family: Telegram
TELEGRAM is a relatively new ransomware, and is a variant of the NEFILIM ransomware. After encryption, all files are encrypted with the ".TELEGRAM" extension. All compromised folders contain a text file called TELEGRAM-RECOVER.txt which contains the email address to which the victim must communicate. Along with encrypting files, this ransomware also moves all the sensitive information to the criminal's server, so the only option is to pay the ransom amount.
Ransomware Family: Loki
Loki is another ransomware written in .NET that encrypts files and changes the filename to recoverdata@onionmail.org, victim's ID, original filename, and the ".Loki" extension. It also changes the desktop wallpaper and displays a pop-up window to indicate that your system is compromised. Additionally, Loki creates a text file called "Restore-My-Files" containing a ransom note. It also instructs victims to contact the attacker through the email ID "recoverdata@onionmail.org". If users try to decrypt the file or use third-party software to recover the contents, it results in irreversible data loss. This ransomware often affects English-speaking users who use Windows and was first detected in August 2021.
Ransomware Family: PHOBOS
The PHOBOS family of ransomware infiltrates a system through Remote Desktop connections. It is a variant of the Dharma or the Crysis ransomware and is believed to be distributed by the same group. Unlike other ransomware programs, PHOBOS does not bypass the User Access Control. This means the UAC window will pop up with the program name 1saas.exe. If the user accepts to run this program (unknowingly), the main process will duplicate itself with elevated privilege and will start encrypting each file on the device. After encryption, a ransomware note is displayed in .hta and .txt formats, and the program will continue to run in the background infecting more files and connected devices.
Ransomware Family: Eking
The Eking ransomware encrypts files and renames them with the victim's ID, "decphob@tuta.io", and ".eking" file extension. It displays a random message in a file and victims must contact the provided email ID. If the victims don't get a response within 24 hours, they are asked to contact the Eking developers through the Tor website. Also, the victim is offered a free decryption option of up to five tools. If the victim sends five files to the developers, they will decrypt its contents. At the time of writing this piece, there are no known tools to decrypt the files encrypted by the Eking ransomware.
Ransomware Family: Mkp
Mkp is a variant of the Makop ransomware and after encryption, it renames the file with the original filename, the victim's unique ID, the cyber criminals' email address, and the ".mkp" extension. A "README-WARNING" text file is created with the ransom note. The information in this file is in a Q&A format and often, comes with a free decryption test. However, many victims did not receive the decryption tools even after paying the ransom.
Ransomware Family: LOCKBIT 3.0
Lockbit 3.0, also known as Lockbit Black, uses a double exhortation method where it encrypts files and exfiltrates them, and if the ransom is not paid, the data is sold on the dark web. The perpetrators often target large institutions like governments, to pay the high ransom amounts. It encrypts files and adds the HLjkNskOq extension. This program also creates multiple threads, so the encryption can be completed quickly, and finally, the victim's desktop wallpaper is changed to notify the attack.
Read and explore how LockBit 3.0 affects the Files and its solutions
Ransomware Family: LOCKBIT 2.0
This predecessor to Lockbit 3.0, also known as Lockbit Red, is also a Ransomware-As-A-Service (RaaS) and is known to have one of the fastest encryption software. It's also one of the most prolific as it's estimated that 26 successful attacks were carried out with Lockbit 2.0. However, Lockbit 2.0 had a few vulnerabilities that were corrected in Lockbit 3.0.
Ransomware Family: MALLOX
Mallox also encrypts files and adds the .malox or .maloxx extension to the infected files. It also creates a ransom note on the desktop and asks the victims to send an email to "mallox.israel@mailfence.com" or "mallox@tutanota.com" email IDs. The cost of the recovery and the account details are shared through email.
Thus, these are some of the prominent ransomware families.
Now that you know what's ransomware and how to identify families based on their attack patterns, read Part 2 to know the common attack vectors and vulnerabilities, along with mitigation and prevention strategies.
Continue Reading the series - Understanding Ransomware Families - Attack Vectors and Prevention Strategies










 7 min read
7 min read







