If you have been in the Mac ecosystem for a while, you probably remember the "Magic T." It was the ultimate IT cheat code. If a Mac refused to boot, or if you needed to move 500 GB of cat videos to a new machine, you simply held down the "T" key during startup. Like magic, the ailing Mac would transform into a glorified external hard drive, its internal storage appearing on another Mac’s desktop as a raw volume.
Target Disk Mode (TDM) was basically the backbone of data transfer, troubleshooting and recovery for nearly two decades. But then came 2020 and with it the Apple Silicon revolution came too. Suddenly, the "T" key just stopped working, the workflow shifted and the expectations of IT professionals and casual users were turned upside down. It turns out that the move to M1, M2, M3, and M4 chips wasn't just about speed… It was actually about rebuilding the Mac’s security from the silicon up.
What Was Target Disk Mode on Intel Macs?
To understand why things changed, we have to look at what we lost (or rather, what was upgraded). On Intel-based Macs, Target Disk Mode was a firmware-level party trick.
How It Worked
When you held "T" at startup, the Mac’s EFI (Extensible Firmware Interface) would bypass the operating system entirely. It would initialize the FireWire or Thunderbolt controller in a "target" state, essentially acting as a hardware bridge between the internal drive and the outside world. The host Mac didn't see a computer; it saw a raw block device… a disk that could be partitioned, formatted, or imaged at a sector level.
Use Cases
This was like the Swiss Army knife of Mac repair. You used it for:
- Rapid Migration: Moving accounts via Migration Assistant before Wi-Fi was fast enough to be useful.
- Diagnostics: Running Disk Utility from a "healthy" Mac to fix a "sick" one.
- Data Recovery: Accessing files when the screen was broken or the OS was corrupted.
- Low-Level Forensics: Creating bit-for-bit clones of a drive for legal or recovery purposes.
The Transition to Apple Silicon
The transition to Apple Silicon (M-series chips) was a total reboot of the Mac’s DNA. We moved from a collection of separate chips (CPU, GPU, RAM, T2 security) to a Unified System on a Chip (SoC).
- New Architecture Overview: This time, the Storage Controller is integrated directly into the SoC. This chip also houses the Secure Enclave, the Neural Engine, and the GPU. This integration allows for incredible performance, but it also means that the storage is "bolted" to the processor in a way that makes traditional "dumb" disk sharing impossible.
- Implications for Boot & Recovery: Because the security model is so tight, an Apple Silicon Mac cannot just "open its gates" to a raw block request from a Thunderbolt cable. To access data, the system must be in a known secure state. This led to the death of classic TDM and the birth of "Mac Sharing Mode," also known as Share Disk, which lives inside the macOS Recovery environment.
What Replaced Target Disk Mode?
The replacement isn't a boot mode; it’s an app that runs inside a mini-operating system.
- “Share Disk” Feature in macOS Recovery: On an M1, M2 or M3 Mac, you just don't hold "T." Instead of that… you hold the power button to enter Startup Options, navigate to Recovery and also to select "Share Disk" from the Utilities menu.
- Key Differences in Behavior
The technical shift here is massive. Instead of presenting a raw disk, the target Mac starts up a specialized SMB (Server Message Block) file server.
- Network Protocol: The host Mac actually connects to the target via a point-to-point network share over the cable rather than a direct-attached storage (DAS) connection.
- Logical Access: You are accessing a "share" not the raw blocks. You can see the files, but you can’t see the "empty" spaces where deleted files might live.
- Authentication Required: You cannot share the disk until you have authenticated with an admin password on the target Mac itself.
Why the Target Disk Mode Changed
Apple didn't do this to be difficult. They did it just to make the Mac the most secure personal computer on the planet.
- Secure Enclave + APFS Encryption: Every Apple Silicon Mac uses hardware-level encryption by default. The encryption keys are tied to the Secure Enclave and a unique hardware UID. If you could simply "read the blocks" via a cable, you would only see gibberish because the data is encrypted at the physical NAND level. The only way to see the data is to let the target Mac's own processor decrypt it first.
- Hardware Design Changes: Since the storage controller is part of the SoC, there is no separate PCIe path that can be easily hijacked by an external cable. The "fabric" of the chip manages the data, and it only hands that data over to a verified, authenticated request.
- Activation Lock & Anti-Tamper Goals: By requiring a password before sharing, Apple ensures that a stolen Mac is a brick. In the old Intel days, Target Disk Mode could sometimes be used to bypass certain OS-level locks. Now, Activation Lock is enforced right at the recovery level.
Practical Impacts on Data Recovery
For the "data rescue" crowd, this change is a bit of a double-edged sword.
- Loss of Raw Block-Level Access: The biggest hit is forensic imaging. You can no longer use a tool to pull a bit-for-bit image of the drive. If a file was deleted and the "pointers" are gone, Share Disk won't help you find the leftover fragments in the unallocated space.
- Dependence on Authentication: If you forget your password and your Mac won't boot, you’re in a tough spot. Without that password, the Secure Enclave won't release the keys to mount the volume in Share Disk mode.
- Behavior After Reboot or Failure: In cases of logic board failure, the data is essentially "cryptographically lost." Since the keys are bound to that specific chip, you can't just desolder the NAND chips and put them on a new board. The "brain" and the "memory" are married for life.
Real Use Cases Today
Despite the changes, the new system works well for most modern tasks.
- Migration Assistant Workflows: Share Disk is still the preferred way to move data between two Macs if you have a high-speed Thunderbolt cable. It handles the "IP-over-Thunderbolt" connection behind the scenes to keep things moving.
- Troubleshooting Boot Issues: If your macOS installation gets corrupted perhaps a bad update or a rogue system extension, you can jump into Share Disk mode and pull your important documents onto another Mac before you wipe and reinstall the OS.
- Hardware Failure Limitations: If the SoC itself is dead, traditional software-based recovery is off the table. This is why "proactive backups" (Time Machine, anyone?) are more critical than ever on Apple Silicon.
Subtle Tool Behavior Context
So, how do professional tools handle this new "fortress" architecture?
Logical Access Is Possible
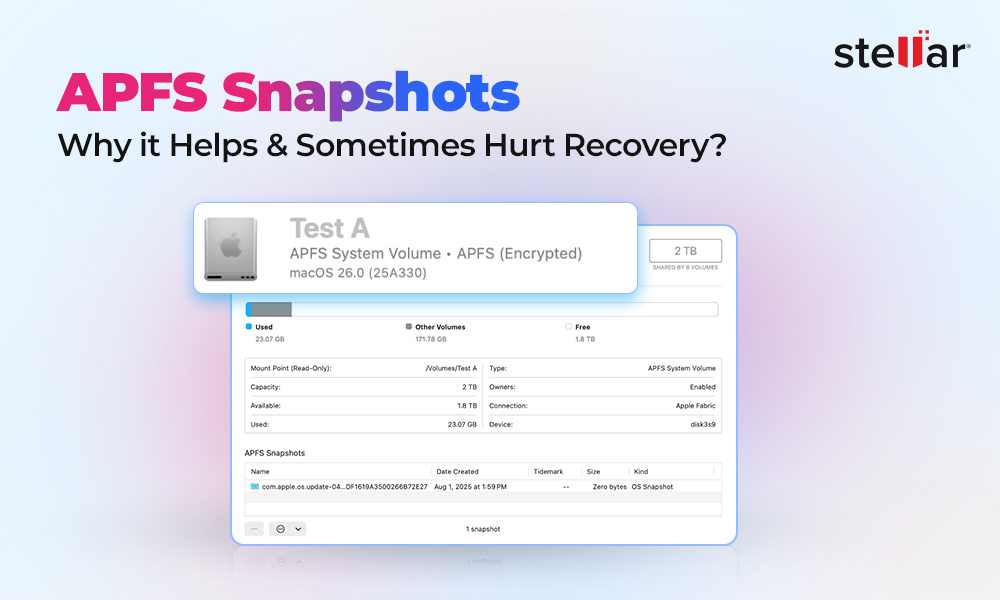
While the hardware is locked down, software has adapted. Modern recovery tools, such as Stellar Data Recovery for Mac, are designed to operate within these new logical boundaries. If you can unlock the disk in Share Disk mode or boot into Recovery, these tools can scan the mounted APFS volumes to reconstruct files that haven't been wiped from the file system.
- Low-Level Access Not Available: It’s important to manage expectations: no software can perform a "sector-level" image of a locked Apple Silicon drive via Share Disk. The tools work by asking the OS (or the Recovery environment) for the decrypted data stream. If the Secure Enclave says "no," the software can't bypass that hardware gate.
- Forensic Handling Considerations: For those in the IT or forensic fields, the workflow now requires "authenticated logical scans." You use the tool to analyze the system while it’s in a powered and authenticated state, ensuring you capture the most data possible before any security timers kick in.
Comparison: Intel Target Disk Mode vs Apple Silicon Share Disk
| Feature | Intel TDM | Apple Silicon Share Disk |
|---|---|---|
| Exposure | Raw block device | Logical APFS share |
| Protocol | PCIe / FireWire Bridge | SMB over IP-over-Thunderbolt |
| Encryption Handling | Handled by Host Mac | Must be unlocked on Target Mac |
| Recovery Potential | Logical + Raw sectors | Logical file access only |
| Forensic Imaging | Full bit-for-bit support | File-level acquisition only |
| Hardware Dependency | Detachable SSD controller | SoC-integrated storage |
Best Practices for Users & Technicians
- Know Your Password: In the Apple Silicon era, your password is the only key to the kingdom. Keep a secure record of it.
- The Right Cable Matters: Don't use those thin white charging cables for data transfers. Those are limited to USB 2.0 speeds. So it is time to invest in a true Thunderbolt 3 or 4 cable that has the lightning bolt logo to avoid connection drops.
- Proactive Backups: Since NAND recovery is almost impossible if that chip fails, just keep an active Time Machine drive or cloud backup, always.
- Don't Reboot During Recovery: If you are in the middle of a scan with a professional Mac data recovery tool… just avoid restarting the target Mac as this will clear the volatile encryption keys from memory.
Key Takeaways for Data Recovery Professionals
For the pros, the game has shifted from hardware hacking to logical reconstruction. Apple Silicon enforces a "logical-only" access path through Share Disk. Stellar Data Recovery for Mac has actually earned the name of the best Mac data recovery software by evolving to handle this and they now are offering compatibility with the latest macOS Tahoe (version 26) and M4-powered systems. These tools can scan native storage without even requiring you to actually disable System Integrity Protection (SIP). It makes them a really powerful tool when the "Magic T" is no longer an option.
Conclusion
Apple’s redesign of Target Disk Mode into Share Disk was a necessary evolution. By moving from a block-level bridge to an authenticated network share, Apple has significantly increased data privacy and security. While this actually makes the lives of data recovery technicians a bit more complicated, it does ensure that your data remains yours even if your Mac falls into wrong hands. Understanding this "Silicon Fortress" is just the first step in mastering the modern Mac.











 7 min read
7 min read