With increasing use of mobile devices in the business world and the option for employees to use their own devices, security and management of such devices have become a top priority for businesses. When employees use their own devices, it doesn’t mean that the company will have full control of the device, but at least it can manage the company’s data and the security requirements of the device.
There are a number of settings and configurations to protect the devices in case they are lost or stolen and to prevent any data being leaked from them. Below, we’ll be discussing such settings and polices that the user can set whenever a company account is configured on the device.
Device Password and Security
Password Requirement
When setting up the Office 365 account on a device, you are required to setup a password. You will not be allowed to setup the work account, if your device is not protected with a password. In devices with Android version 10.0 or later, Google has removed the device admin functionality. Now, the secure application or work profiles require the use of new APIs. It is now more secure as the app is not aware of the user’s device password and only aware of the complexity of the password.
Password Length
With the above option, you can also specify the character length of the password.
Password Complexity
The password should include numeric PIN or special characters. Although most of the devices nowadays have biometrics, like Apple Touch ID or Face ID, these cannot be controlled by the PIN or compliance of the company.
Android devices support a number of password complexity levels. Mostly, businesses use the High level as it would require a pin with no repeating or ordered number sequences with a minimum of 7 characters, an alphabetic password with a minimum of 6 characters, and an alphanumeric password with a minimum of 6 characters.
Timeout Locks
A policy can be defined to specify the time until the screen locks and the password is needed to unlock.
Wipe Device after a Number of Failed Attempts
Companies would opt to enable this feature. If there are more than a stipulated number of attempts to unlock the device, this would end up in wiping the device.
Mobile Device Mailbox Settings
Apart from the security point of view, the company would need to have other setting options to lock down the company-owned devices to prevent the leak of data or breach of devices. Though there are a lot of settings, we will be discussing below some commonly used mobile device settings.
Bluetooth
You can disable the Bluetooth option completely or enable it for hands-free only.
Camera
You can disable or enable the use of the camera (front and back) on the device.
Internet Sharing
You can disable or enable the feature to allow internet sharing and allow other devices to use the device for internet access.
Device Encryption
This setting enables encryption on the device. Unfortunately, not all the devices can enforce the encryption.
Approved Application List
This setting specifies the approved applications that can run on the device.
Allow Unsigned Applications
This is disabled by default. It’s good to not allow users to install applications which are not signed.
In addition to above, there are several other Mobile Device Management (MDM) policies and settings. If you are looking to add extra security and deeper management of the mobile devices, you need to add Enterprise Mobility and Security (EMS) to the Office 365 subscription to use Intune to fully manage the devices, their applications, and for more advanced controls.
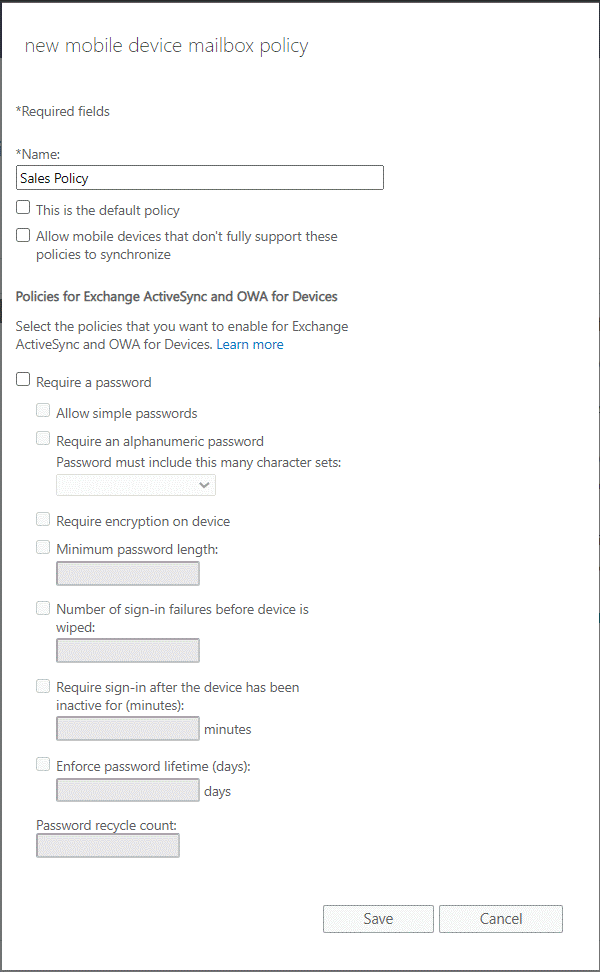
Accessing the Policies
Once you have accessed the Exchange Admin Center, click on Mobile and then Mobile Device Mailbox Policies. Click on the Add + button to create a new policy. The policies can also be managed using the PowerShell commands and connecting to the Exchange Online tenant.
Conclusion
The mobile device mailbox policies can come really handy when you need to manage mobile devices. This will ensure some manageability of the devices and security of the business data. When migrating to Office 365 or local Exchange Server with a hybrid setup, you might set up such policies, active sync policies and other policies, like retention before the migration.
Creating the policies incorrectly might result in unintentional data loss. Re-importing data from an old or decommissioned Exchange Server can be an administrative burden. In such a case, you can use applications, such as Stellar Converter for EDB. By using the application, you can open any EDB file from any version of Exchange Server, browse through the data store, and granularly export to PST and other file formats. You can easily export data from EDB file to a live Exchange Server database or Exchange Online with automatic mailbox mapping, parallel and priority exports, and continuation in case of interruption.













 4 min read
4 min read







