iPhone loyalists swear by the robust data security measures provided in each iOS device. Nonetheless, a unique combination of a six-digit passcode is not adequate to restrict thieves from digging out most confidential data from your stolen iPhone. They are experts at fooling iPhone users to disable Activation Lock by remotely eliminating stolen iOS device from the iCloud.
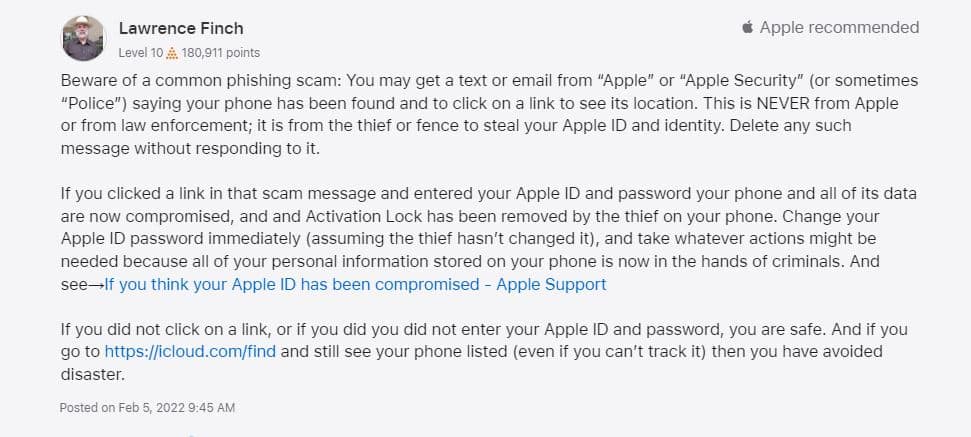
In the above-mentioned Apple support query, an iPhone user alerts others of possible scams after losing their iPhone in an unforeseen mishap. It is clear that as soon as your precious iPhone gets stolen, you become vulnerable to phishing scams and various other traps planned by scammers.
To counter such threats, you must stay cognizant of what do people with stolen iPhones, but before that follow these immediate action plan to prevent possible damages like data loss.
What do I do if my iPhone is lost or stolen?
First of all, try locating your iPhone with 'Find My' app on iCloud. If you have enabled 'Find My iPhone' feature in the stolen iPhone, it would be easier for the app to locate your iOS device worldwide on the map.
Simply sign in to icloud.com using your apple ID and password and select your stolen device using All Devices drop down menu on the Find My iPhone's map interface. Eventually, the app will start tracking the exact location of your lost iPhone on the map.
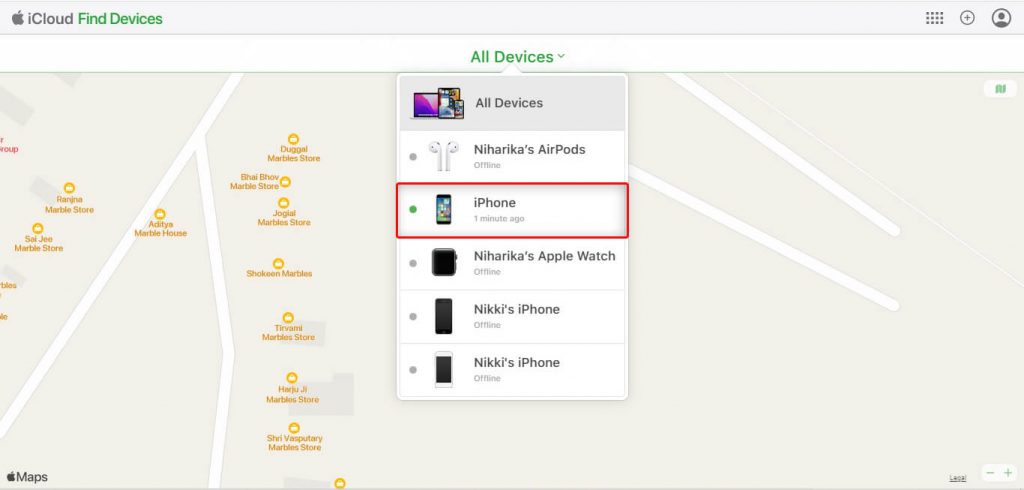
Note: A green dot against the device name is an indication of online while a grey dot indicates the device remains offline.
If your iPhone is already out of reach as per the location traced through Find My app, follow these immediate action plans to protect all the personal and confidential data stored in it.
Mark your iPhone as lost
Apple is known for its flagship features. It gives you the liberty to mark your iPhone as stolen or lost remotely. Use Lost Mode to keep your iPhone's data passcode protected. As a result, the confidential information stored in a stolen iPhone remains secure. You can also display a custom message with your mobile number on the Locked Screen while keeping track of the live location of your stolen device. Use steps mentioned below to mark your iPhone lost:
- Login to the Find My app using Apple ID and Password.
- Select the stolen iPhone from the drop-down menu.
- A tiny box will open at the left side on iCloud Find Device screen with three options – Play Sound, Lost Mode, and Erase iPhone, all highlighted in green.
- Click on Lost Mode to activate or turn on this option.
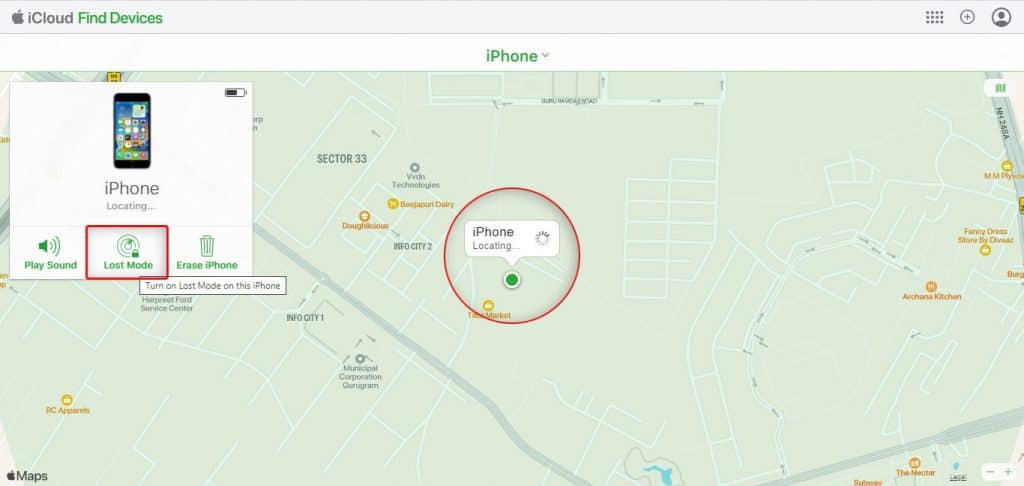
- Follow the screen instructions if you wish to display your contact number on the missing iPhone.
- You can also enter a custom message, at this stage, requesting the finder of your missing iphone to contact you immediately.
- Select Activate to proceed forward.
Extract iPhone Data from iCloud or iTunes Backup
Most iPhone users are well-versed with the automatic iPhone data backup option on iCloud or iTunes. Key benefits of these backup systems is that you can recover your confidential data from either of the options if your iPhone was stolen or lost and erase everything before the hackers access your lost iPhone. The only disadvantage of iCloud and iTunes data recovery is that you don't get to choose the files, photos, or specific amount of data for backup. As a result, the data retrieved from stolen iPhone takes a lot of space in your computer.
To overcome this problem, use a third-party iPhone data recovery software like Stellar Data Recovery for iPhone. The software gives you the benefit of extracting a selective few files, folders, photos, and documents from iCloud or iTunes. It deploys a robust scanning algorithm to extract a limited set of data, which is necessary to prevent possible losses with the stolen iPhone. Refer to this blog to recover data from lost or stolen iPhone in simple steps. You can also recover lost photos from the stolen iPhone by following guidelines suggested in this blog.
Remotely erase your iPhone
Wouldn't it be idyllic if your stolen iPhone could self-destruct all the data stored in it in a bid to keep scammers distant from your personal and confidential data from stolen iPhone? Definitely, the device won't explode, but Apple does give you the opportunity to wipe of iPhone data remotely. Follow this link to learn how to remotely erase stolen iPhone using iCloud with 'Find My' app. Although, you are advised to imply this option only after extracting significant amount of personal data following the options mentioned in the previous point.
Enable 2FA and change password
Despite all your efforts to lock iPhone remotely, possibilities are high that the thief can get access to your iPhone for a short duration in which they can cause enough financial harm.
So, prioritize regularly changing password of personal and official emails accounts, social media accounts, mobile banking and investment apps, shopping apps, online streaming apps, etc. In case you have enabled auto-saving passwords on Safari, your credit card details could be at risk of exposure. So, update all the passwords with unique and secure passwords. Also, enable two-factor authentication to add a double layer of security on all accounts without using SMS for 2FA codes as your phone is in wrong hands. Use an authenticator app like Google Authenticator.
Terminate credit card linked to Apple Pay
Contact your bank on priority to cancel your credit card that was linked to digital wallet like Apple Pay. Muggers can use it to make unauthorized purchases. You can also request the bank to update their fraud department about any recent dispute or fraudulent activity. Further, closely monitor your bank account statements in the weeks and months following the iPhone theft for any dubious charges.
Alert people and Block your SIM and IMEI
Scammers can text, call, or reach out to your family and friends for sensitive information or money. Spread news about your device loss among knowns to keep them aware of the possible smishing scams impersonating you. You can file a complaint and demand immediate SIM block on the grounds of the device being lost or stolen. As a result, scammers remain inefficient of using your phone. Inform your local security agencies to speed up the iPhone recovery process. Keep the serial number of the stolen device handy to help the cops commence the terminal search.
What Do People Do with Stolen iPhones?
Over the years, iPhone has become the most sought after mobile device among teenagers and adults, but not everyone can afford it. This disparity has fuelled the demand of stolen iPhones in the secondary market where anyone can buy expensive iOS device at an affordable price. Even though, the idea of your iPhone being stolen is absolutely undesirable, it is essential for all the users to learn what do people with stolen iPhones:
Blackmail attempt and other damages
After stealing an iPhone, thieves look for smart ways to access your personal or confidential data like banking and investment details stored in mobile apps and digital wallets. There are many free data recovery software available online. Scammers can use them to extract your personal data from iPhone and blackmail you for it. Your social media and email accounts, photos, and passwords, all are jackpot for them.
Sell iPhone parts in secondary market
If the burglars can't retrieve iPhone data, they dismantle the iOS device and sell each part in the secondary market. Be it screen and input, 3D Touch, Haptic Touch, Sensors, Audio and output, Battery, Camera, or even SIM card holder, each element is costly enough to give them a decent reward.
Screen Replacement
Thieves can break the screen of stolen iPhone and seek AppleCare support for its replacement. After gaining access to your iPhone, they can convince the AppleCare team to replace the screen if the stolen phone is in the warranty period. If not, nowadays, a wide range of substitutes and duplicate elements are available that look as good as new to put your iPhone back on the shelf for resale.
Make Unauthorised Payments
After stealing and gaining access to personal data, scammers can make unauthorised payments and fraudulent purchases with your digital wallet like Apple Pay. They can also access your investing apps in order to wire out your saved details. Some iPhone users make this common mistake of using similar password for all the apps for online purchases. Also, they keep Notes of the login details saved in their iPhones. Such habits are an open invitation to unwanted financial losses.
Malware scams like Phishing emails and texts
After losing iPhone, you may possibly receive alarming messages like 'Your Apple account is now locked' or an elaborate email on the same lines. Beware! These are attempts to phishing attack, a common practice used by hackers to get seamless access to the stolen iPhone. Avoid becoming a victim of phishing scams and never unveil your Apple login details to anyone. Moreover, avoid hitting any shortened URLs or dubious links. Always check spelling mistakes and grammatical errors to identify phishing attempts.
The list of possibilities goes on.
Conclusion
Despite the evident stress of data theft, iPhone fans continue spending thousands of dollars to buy upgraded model. Though, no harm in taking precautionary measures while carrying an expensive device. So, be watchful of what do people with stolen iPhones and dodge fraudulent activities happening around iPhone users. iPhone thieves will continue stealing and reselling pricey iOS devices in the secondary market. So, be careful when using iPhone in crowded areas. Moreover, if you accidentally lose an iPhone, don't fall in the trap of phishing scam that thieves may spell to steal your Apple ID and unlock your stolen iPhone.














-1847.jpg)
 8 min read
8 min read







