To investigate cases related to cyber-crimes where emails are being used, digital forensic experts scan relevant emails for evidence. Since criminals often forge messages to avoid detection, email forensics experts need to perform email header analysis to extract and collect crucial evidence.
Email headers contain vital information about the path that the message has traversed before reaching its final destination. This information includes recipients' and senders' names, time of sending and receiving the email message, email client, internet service provider (ISP), IP address of the sender, etc. This information and other email header fields can help in determining the legitimacy of a suspicious or malicious email.
Email Header Analysis in Gmail
To view the header of a Gmail email message, follow these steps:
- Go to your Gmail Inbox and click the email whose header parameters you want to see.
- Next to the Reply icon, click the dropdown menu icon and select Show original.
This will display email header parameters in a new window. You can either go through these parameters directly or copy and paste the text in Google's email header analyzer for better visibility. This tool will highlight the parameters in the entire text.
To understand email header fields in Gmail, we take a message of a sender as an example. [See Figure 1]
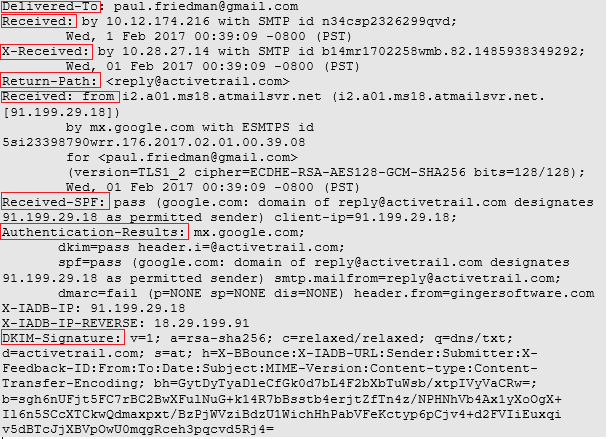
Figure 1: Email header analysis in Gmail
1. Delivered-To
Delivered-To: paul.friedman@gmail.com
This email header field contains the email address of the intended recipient. It is one of the major things to check during email analysis as it can provide details of phishing activities. If the email address in this field is not the same as the recipient's actual email address, then it can be a sign of message tampering that warrants an investigation. It's worth noting that email header tampering and spoofing is rather easy for cybercriminals these days - all they need is a Simple Mail Transfer Protocol (SMTP) server and mailing software to launch a phishing attack.
2. Received By
Received: by 10.12.174.216 with SMTP id n34csp2326299qvd
Wed, 1 Feb 2017 00:39:09 -0800 (PST)
This field contains the details of the last visited SMTP server. The following information is disclosed:
Server's IP address
SMTP ID of the visited server
Data and time at which the email was received by the SMTP server
3. X-Received
X-Received: by 10.28.27.14 with SMTP id b14mr1702258wmb.82.1485938349292;
Wed, 01 Feb 2017 00:39:09 -0800 (PST)
Some email parameters are not defined in Internet Official Protocol Standards and are called non-standard headers. These are created by mail transfer agents like Google mail SMTP server which may use the X-Received field to share the non-standard information. This field must not be overlooked during email header analysis as it shares the following details:
IP address of the message-receiving servers
SMTP ID of the server
Data and time at which the email was received
4. Return Path
reply@activetrail.com
This field contains the email address where the message is returned, in case it fails to reach the intended recipient. This can easily happen if the sender has used the wrong email address for the recipient.
by mx.google.com with ESMTPS id 5si23398790wrr.176.2017.02.01.00.39.08
for (paul.friedman@gmail.com)
(version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Wed, 01 Feb 2017 00:39:09 -0800 (PST)
This field contains the information of the first SMTP server where the email was reached. The following details can be found here:
Server-related IP address
Receiver's email address
Encryption information
Data and time at which the message was received
5. Received From is one of the most important fields in an email header as you can find the IP address of the sender along with other details like the hostname.
6. Received-SPF
Received-SPF: pass (google.com: domain of reply@activetrail.com designates 91.199.29.18 as permitted sender) client-ip=91.199.29.18;
Sender Policy Framework (SPF) is an email security protocol that is used to verify the sender. The system forwards the message only after the sender's identity is authenticated. The technique uses the domain address for authentication and adds the check status in the header field. The following codes are used:
Pass: Email source is valid
Softfail: Fake source possible
Fail: Source is invalid
Neutral: Source validity difficult to ascertain
None: SPF record not found
Unknown: SPF check can't be performed
Error: An error occurring during SPF check
7. Authentication Results
Authentication-Results: mx.google.com;
dkim=pass header.i=@activetrail.com;
spf=pass (google.com: domain of reply@activetrail.com designates 91.199.29.18 as permitted sender) smtp.mailfrom=reply@activetrail.com;
dmarc=fail (p=NONE sp=NONE dis=NONE) header.from=gingersoftware.com
Mail Transfer Agents (MTAs) apply a slew of authentication techniques to the email messages before processing them. The results of these techniques are added to the header field of messages and are separated by a semicolon.
The Authentication-Results field is of great importance in email header analysis forensics as it shares the ID of the authentication performing server. It also shares the authentication techniques along with their results.
8. DKIM Signature
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; q=dns/txt; d=activetrail.com; s=at; h=X-BBounce:X-IADB-URL:Sender:Submitter:X-Feedback-ID:From:To:Date:Subject:MIME-Version:Content-type:Content-Transfer-Encoding; bh=GytDyTyaDleCfGk0d7bL4F2bXbTuWsb/xtpIVyVaCRw=; b=sgh6nUFjt5FC7rBC2BwXFulNuG+k14R7bBsstb4erjtZfTn4z/NPHNhVb4Ax1yXoOgX+ Il6n5SCcXTCkwQdmaxpxt/BzPjWVziBdzU1WichHhPabVFeKctyp6pCjv4+d2FVIiEuxqi v5dBTcJjXBVpOwU0mqgRceh3pqcvd5Rj4=
DKIM signature header field is inserted in an email message to share details of the sender, message, and the public key which is required to perform message authentication. Many email platforms like Gmail and Outlook.com support this field to confirm email authenticity.
Here are the various tags of the DKIM signature header:
- v: application version. Only version 1 exists today so this field should always be set to 1.
- a: algorithms used for encryption. It should be rsa-sha256 in most cases. Some senders may use rsa-sha1 but it's not recommended due to security risks.
- c: algorithms used for canonicalization.
- s: selector record name used with the domain.
- h: signed header fields that are used in the signing algorithm to create the hash in b= tag.
- bh: hash of the message body.
- b: hash data of the headers listed in the h= tag. It's also called DKIM signature.
- d: domain used with the selector record.
Note: All the above tags are required for the DKIM mechanism to work. If any tag is missing, then verification may encounter an error. Although, other optional tags may or may not be used, like t= (DKIM timestamp) and c= (canonicalization algorithm used).
Other Important Email Headers
X-BBounce: 227254537|1486804|paul.friedman@gmail.com|47|0|3605|4
X-IADB-URL: http://www.isipp.com/iadb.php
Sender: Ginger (noreply@gingersoftware.com)
Submitter: reply@activetrail.com
X-Feedback-ID: 3605:3605.1346802.0:G1:atgfbl
List-Unsubscribe:(http://trailer.web-view.net/unsubscribe/0XE838F4BC62366CBC595D7E381467599CE32C9B2368C35B4CB7315919D29140E3552835B8FF6C759D.htm),
Reply-To: Newsletter@gingersoftware.com
From: Ginger : (noreply@gingersoftware.com)
To: "paul.friedman@gmail.com" : (paul.friedman@gmail.com)
Message-ID: (c000e5f41f8f4137a30cab4g6eddcd1e@gingersoftware.com)
Date: Wed, 01 Feb 2017 10:39:06 +0200
Subject: Thank you for registering with Ginger!
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary="----7308DF8A8DBB43098928C652849D6409"
------7308DF8A8DBB43098928C902849D6409
Content-type: text/plain; charset=utf-8
Content-Transfer-Encoding: quoted-printable
Reply-to: The email address at which the reply to the message is received. It's usually the sender's email address but may also be changed manually.
From: Sender's email address.
To: Receiver's email address.
Message-ID: Unique ID of the email that makes it distinguishable. No two emails can share the same message ID.
Date: Date and time at which the email was received at the destination.
Subject: Email subject section that contains the main purpose of the message.
MIME-Version: This shows that the message is Multipurpose Internet Mail Extension (MIME) formatted and can support formats, like plain text files, video, audio, etc.
Email Header Analysis in Outlook
Email analysis and the process of extracting email headers can vary from one Outlook version to another. Below are the steps for extracting email headers in different Outlook versions.
Outlook 2019, 2016, 2013, and 2010
- Launch Outlook and double-click the email whose header parameters you want to see.
- Go to File > Properties. This will open the Properties window.
- Refer to the Internet headers section. Here you can find the header parameters.
Outlook 2007
- Launch Outlook and double-click the email whose header parameters you want to see.
- Under the Message tab, in the Options section, click the Dialog Box Launcher icon (the arrow button). This will open the Message Options window.
- Refer to the Internet headers section.
Outlook 2003, 2002, and 2000
- Launch Outlook and open the email in a new window whose header parameters you want to see.
- Go to View > Options. This will open the Message Options window.
- Refer to the Internet headers section.
Email Header Analysis
By analyzing the key parameters in an email header, you can get an idea of how the message traveled from the source to the destination. For instance, you can use the originating IP to find the original sender. For this, you need to examine the first Received parameter in the email header. The first IP address here is the originating IP which is also sometimes presented in the fields X-Originating-IP or Original-IP. Borrowing the same header example:
Received: by 10.12.174.216 with SMTP id n34csp2326299qvd; Wed, 1 Feb 2017 00:39:09 -0800 (PST)
The highlighted portion is the original sender of the message. You can use a free reputation service like SenderBase by Cisco to get the reputation rating of the IP. This can help ascertain whether the email is spam or a phishing attack. Although, bear in mind that if the IP address is private, then it may not fetch any result.
Message-ID is another important field that can be checked during email header analysis for spoofing. You can see it below in the highlighted region.
Reply-To: Newsletter@gingersoftware.com
From: Ginger (noreply@gingersoftware.com)
To: "paul.friedman@gmail.com" (paul.friedman@gmail.com)
Message-ID: (c000e5f41f8f4137a30cab4g6eddcd1e@gingersoftware.com)
Date: Wed, 01 Feb 2017 10:39:06 +0200
Subject: Thank you for registering with Ginger!
MIME-Version: 1.0
Since Message-ID is added by the mail server that processes the email, it can't be altered. Also, message systems often use a date/time stamp, along with the sender's domain name. So, if the domain name in the message ID doesn't match the domain name mentioned in the From: field, then it can suggest a possibility of spoofing. In the example above, the From: field shows the domain name gingersoftware.com, which is same as the Message ID. So, it's safe to assume that no spoofing took place here.
Significance of Email Headers
Email headers are replete with useful details, like originating IP address and message ID that can be instrumental in investigating and tracking the suspicious email. However, to identify critical details that can point you in the right direction, you must have a good understanding of email header analysis. In most cases, even if you know about it, you need to use a specialized email forensics tool to gather and preserve evidence in the form of reports and email files. Tools such as Stellar Email Forensic provide advanced features such as custom search filters, multiple message views, deleted email recovery, etc. that contribute to the speedy and accurate investigation. You can start with evaluating Stellar Email Forensic software, presently available for a 60-day free trial. It offers a case management facility and allows one to perform a granular search for emails.










 8 min read
8 min read







