What is Email Spoofing?
Email spoofing is forging a sender's email address to mislead the recipient. Usually, the sender intends to deceive the recipient into the opening and responding to the email message. This way, the sender tricks the receiver into sharing sensitive information, like clicking a malicious link.
Email spoofing seriously threatens the IT security of any organization (or individual user), where just one phishing attack can cause irreversible damage. In addition, it can lead to the theft of trade secrets or a massive data breach that can hurt a company financially, malign its reputation or even lead to legal action. Therefore, it is critically important for companies to be aware of such risks and understand how email spoofing is performed.
Types of Email Spoofing
1. Display Name Deception
In this, the scammer or malicious sender poses as a reputable and legitimate brand to dupe the recipient by sharing personal details, financial transaction details, etc. This email spoofing technique exploits a common feature of email clients, especially on mobiles. These email clients display only the name of an email sender. So, a receiver may think they have received the email from a trusted entity, whereas in reality, the email address belongs to a malicious sender.
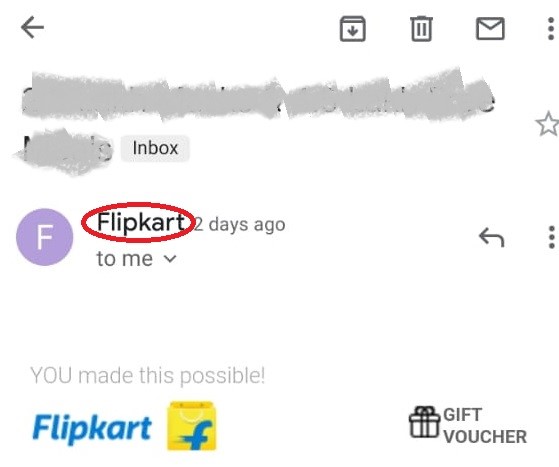
Figure 1: An Email item viewed on Gmail mobile app
The above image shows an email received on Gmail mobile app. It is to be noted that the app only shows the name of the sender (Flipkart, a reputable and well-known brand) by default rather than the actual email address. However, the sender with any random email address can set the name as Flipkart, which is visible to the receiver instead of the email address. This is a common way of deceiving email recipients about the sender's actual identity.
2. Domain Spoofing
When a malicious email sender disguises themselves as a representative of a trusted company by using a fake domain name, one that appears to be from the company rather than the sender's, it is known as domain spoofing. Not all email services verify domain ownership when someone sends an email. Instead, cybercriminals manipulate the email protocols of these services to display the desired email address in the "From" header, along with the name.
3. Email Injection Attacks
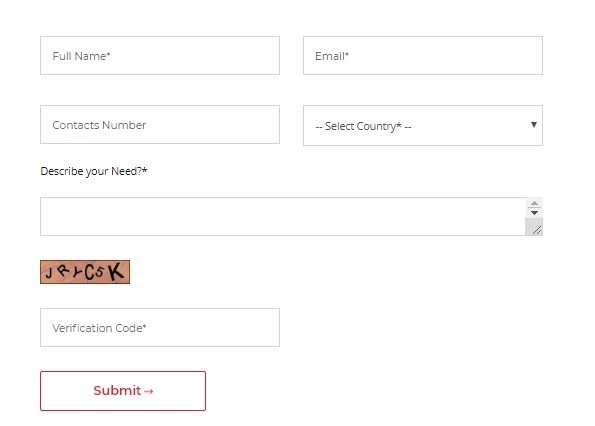
Figure 2: A dummy contact form commonly used on websites for collecting user information
Many websites and web applications use contact forms (as shown in Figure 2) to collect user inquiries, registration details, etc., triggering emails to the webmaster or IT admin. These forms often use headers processed by the email library on the webserver. The interpretation generates SMTP commands, which are then handled by the appropriate SMTP server to transmit the message successfully. In most cases, everything will work seamlessly, and the messages will reach the recipients without a problem. However, there is a risk that if a user's message is not validated before it is processed, then this may make the contact form more vulnerable to Email Header Injection, i.e., SMTP Header Injection attack. Simple Mail Transfer Protocol (SMTP) is a set of communication guidelines that allow the transmission of an email from sender to receiver across the Internet. It can interpret different commands that are shared by email.
An email can be divided into two parts:
- Body
- Envelope
Email body is the message that the sender wants to transmit. The envelope contains different commands that SMTP can interpret. The following are some of the commands that you need to know:
- MAIL FROM: Adds the message sender.
- RCPT To: Adds the message recipient. It is used multiple times, to deliver a message to multiple people simultaneously.
- DATA: Informs mail-server that message data, which includes email header and body text, shall be sent along with the rest of the fields.
It's important to remember that email headers are not part of the SMTP protocol. Email clients use them to display emails in a standard format. The following are some email headers that you need to know:
-
From: Adds a sender. This email address can be different than the MAIL FROM email address.
-
To: Adds the recipient(s). This can be different than RCPT TO content.
This is an example of SMTP communication:
- > MAIL FROM:(yourenemy@email.com)
- < 250 OK
- > RCPT TO:(victim@useremail.com)
- < 250 OK
- > DATA
- < 354 Send message content; end with (CRLF).(CRLF)
- > Content-Type: text/html
- > Date: Wed, 15 April 2020 00:04:05
- > From Your Friend : (yourfriend@email.com)
- > Subject: Need Your Help
- > To: Victim (victim@useremail.com)
- >
- > Hey Pal!
- > Hope you are doing well. Actually, I am writing to you coz I need money on an urgent basis. It's for my mom's emergency surgery. I will call you later to explain but for now, I am not asking for a specific amount. Just please send as much money you are comfortable parting with. Here is the link to my bank account: www.maliciouswebsiteaddress.com . Please try to send as soon as you get this.
- > --
- > Love You Man!
- > Your Friend
- > .
- < 250 OK
The above email will be received by victim@useremail.com. However, they will see that it was sent by yourfriend@email.com (not yourenemy@email.com). This is how a cybercriminal can deceive the recipient.
Email libraries in web programming languages usually don’t allow you to add envelope commands. However, if you supply email headers, the libraries can convert these into appropriate SMTP commands. Unfortunately, this functionality is exploited by cybercriminals as they can use specific email headers, which are converted into appropriate SMTP commands.
4. IDN Homograph Attacks
Take a look at the following domains:
www.ɡoogle.com
www.google.com
They both are Google's web addresses, right? Unfortunately, the answer is a "NO". The two websites may look identical to an average web user, but for a computer, there is an important distinction between them. The "g" in the first URL is a Latin small letter script whose Unicode Hex is U+0261. In the second URL, it is the Latin small letter G whose Unicode Hex is U+0067. Computers can identify this difference and treat domain names differently.
Many familiar characters in the Latin letter system look the same, but their hexadecimal values are different. As a result, the letters, called homoglyphs, can pose serious security threats. Let us look into an example to understand the problem in a real-world scenario.
We all know the technology giant Apple. Apple Inc. has an official website whose URL address is www.apple.com. However, someone can use a visually similar domain name, such as www.apple.com, in which the a and e characters are borrowed from the Cyrillic letter system and have different Unicode values (U+0430 and U+0435 compared to Latin letter system in which the Unicode values for these letters are U+0061 and U+0065). So, if someone receives an email, where the sender’s email address, visually appears as customercare@apple.com, they might believe it to be from Apple Inc. Trusting this email will be easy for the recipients and they may fall for a phishing attack.
Note: In your email preview, both customercare@apple.com and customercare@apple.com will look visually identical.
How to Prevent Email Spoofing?
- Be careful while opening email attachments. Pay special attention to the email subjects that have a sense of urgency.
- Question the content, generic greetings, salutations, and email body content in the emails from Unknown senders. Whenever you receive an unsolicited message, always question the content of the message. If the message is requesting any personal information or directing the user to some external links or open attachments, it is a warning signal that the email has been spoofed.
- Investigate the puzzling context, like emails with photos of another employee's vacation, documents of a meeting that never took place, etc.
- Make sure to adjust spam filters, so emails containing malicious links or attachments do not land in the inbox.
- Spoofing Attacks such as Email header injection can be mitigated by validating users' input in contact forms. You should ensure that a user isn't able to add any newline characters in the message, as these characters can allow attackers to append email headers. A simple way to achieve this is to create and implement a whitelist of authorized characters.
- To prevent homograph attacks, you can configure browsers, so they don't support Internationalizing Domain Names in Applications (IDNA). You can also block International Domain Names (IDNs) websites that use different scripts like Cyrillic.
- While surfing the Internet, stay away from suspicious websites.
- Install and maintain the excellent quality antivirus-antimalware program. Keeping the operating system and software, up-to-date will ensure they are protected against the latest threats.
- Avoid sharing personal, confidential information related to the finances over emails.
- The SPF (Sender Policy Framework), DKIM (Domain Key Identified Mail), and DMARC (Domain-Based Message Authentication, Reporting, and Conformance) validations should be set up correctly by the security operations center team.
- Carefully check the Email Header Information. The email headers contain a good amount of information regarding the hop path traveled by the email. Ensure that the 'From' email address matches the display name and the 'Reply-To' header matches the source. Pay close attention to the 'Return-Path' field as well.
- Use a strong and complex email password that is difficult to guess and crack by hackers.
Using an eDiscovery and Email Investigation software
Stellar Email Forensic is an advanced software for email search that analyzes and investigates mailbox data of various email clients, email services (such as Exchange, Office 365, GroupWise Server, Google Mail, Notes, etc.), and email backup files with 100% accuracy. This software allows email investigation across more than 25 file formats, such as EDB, PST, OST, DBX, NSF, MBOX, OLM, TBB, EML, etc., through a single interface. In other words, it helps in digital evidence collection. Another great feature of Stellar Email Forensics is that it allows case management during criminal investigations through tagging, bookmarking, and logs. In addition, this tool generates customized litigation reports. To produce the evidence in a court of law, bulk email forensics is also required, as there are high chances that the after-effects of the cyberattacks have spread at a large scale. The evidence is preserved with MD5 and SHA1 hash values while extracting and analyzing the data.










 8 min read
8 min read







