Decision-makers in the IT industry are well-aware of email phishing attacks that have become rampant. These include Business Email Compromise, in which companies are tricked into paying fake invoices, and whaling phishing, in which the attackers target high-profile executives, like CFOs and COOs, to steal sensitive information. Unfortunately, technology giants like Google and Facebook aren't safe as they were duped out of over $100 million during 2013-15 in a massive fake invoice scam.
Basic security measures like firewalls and Internet security software are not enough to ward off email phishing attacks. It would be best if you had a deeper understanding of your company's email setup for better protection. For that, you need advanced tools like professional email forensics software. These programs can help you parse and study every email your company sends and receives to identify potential email phishing attacks and limit damage even in situations when an attack has already taken place. However, before you do that, you can consider implementing email security protocols, such as DKIM, SPF and DMARC.
What are DKIM, SPF and DMARC?
DKIM, SPF, and DMARC are security techniques that allow you to authenticate your emails. They also inform mail services, ISPs, and other email receivers that certain third-party entities are authorized to send emails on your behalf. These protocols can serve as powerful anti-spam and anti-phishing measures when used together.
Types of Security Protocols
To maintain security on all email frontiers, the three pillars of protocol-based security, i.e., DKIM, SPF, and DMARC, must work together. This is because each of them serves a different purpose. For example, SPF defines which mail servers are authorized to send emails on your behalf, DKIM adds digital signatures to your messages for authentication, and DMARC defines how SPF and DKIM work together. DKIM also offers a reporting feature.
What is DKIM?
Domain Keys Identified Mail (DKIM) is an email authentication technique that allows you to verify if an email is sent and authorized by the sender. This is done with a DKIM signature, an encrypted digital signature added to an email message. Once the receiver confirms that an email is signed with a genuine DKIM signature, it means that the contents of the email aren't tampered with.
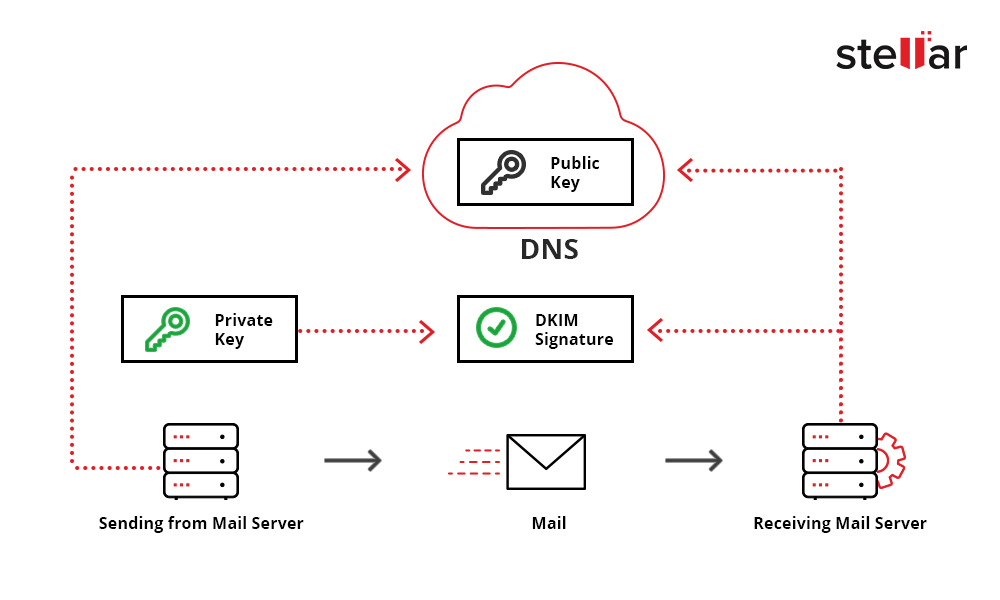
Figure 1: Schematic Layout of DKIM
Mail Transfer Agent creates a hash value for a DKIM signature, which is kept in the listed domain. The email receiver can use the public key registered in the DNS to authenticate the signature. If the signatures obtained from the decryption of Hash Value in the email header and the email are identical, the Mail Transfer Agent can know for sure that the email isn't tampered with along the passage.
You can set up DKIM with just three steps:
- Generate the domain key for your domain. There are many key generators, such as PuTTYgen, that you can use. You can download PuTTYgen.
- Add the Public Key to your domain's DNS records.
- Turn on DKIM signing to start adding DKIM signature to all emails that you send in the future.
For example, you can use DKIM milter, an open-source service. It can be downloaded from here.
What is SPF?
Sender Policy Framework (SPF) is another email authentication technique that can check domain spoofing and prevent spammers from sending messages on behalf of your domain. It comprises three components: an authentication function, specialized headers placed in emails, and a policy framework.
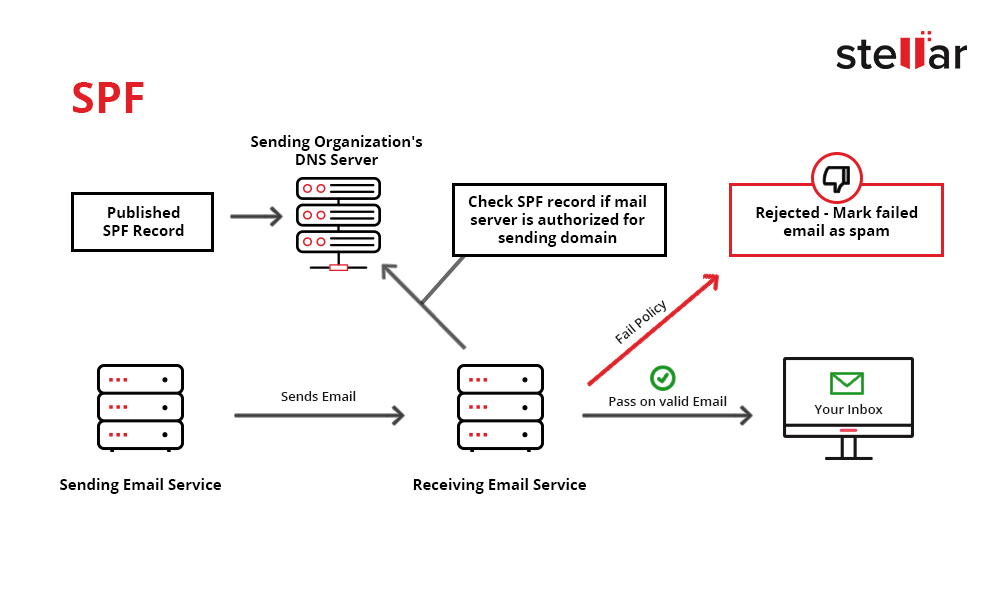
Figure 2: Schematic Layout of SPF
An SPF record is a record that's added to your domain's DNS record. It contains the IP addresses you want to authorize for emailing on your behalf. This can come in handy if you use a hosted email solution like Google, Apple, Office 365, or an ESP like Higher Logic.
In the SPF technique, the receiver of your email can use the "envelope from" address of the message to confirm that the sending IP address is authorized for delivery. If the sending email server is absent in the SPF record, the email is flagged and rejected by the email receiver.
Sample SPF DNS TXT Record
The following is an example of SPF record:
| Tag | Meaning |
| v= spf1 | SPF version used. 1 is the only version available now as version 2 was discontinued |
| Ip4 | IP address/range |
| Ip6 | IP address/range |
| Include: | For external domains. Trusted external domains can be added here that may include Salesforce, Mailchimp, etc. |
| No other features | Offers video editing, GIF creation, subtitles, overlay, etc. |
| ~all | Only the domain's mail servers and those in the "a" and "include" sections are authorized to send emails for the domain |
Your SPF record should look something like this:
v=spf1 ip4:34.243.61.237 ip6:2a05:d018:e3:8c00:bb71:dea8:8b83:851e
include:thirdpartydomain.com -all
What is DMARC?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is a protocol that binds DKIM and SPF together. It lays down a clear policy for both and creates an address that can be used to send reports of email messages collected by the receivers against a particular domain. It also provides a mechanism to determine if an email is rejected after implementing the SPF protocol.
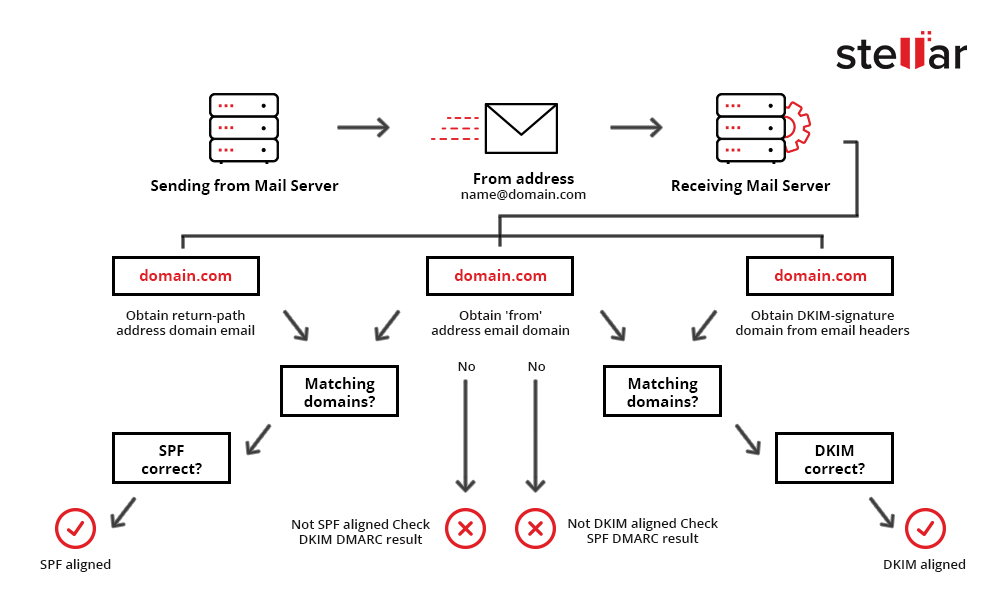
Figure 3: Schematic Layout of DMARC
To deploy DMARC, you have to create a DNS record for the domain you want to use in the FROM: address. You can put multiple values in the record but you have to at least include the following two:
- (v) directs the receiving server to implement DMARC
- (p) tells the server what to do in case authentication fails
Setting up SPF, DKIM, and DMARC
SPF, DKIM, and DMARC are robust email security protocols. However, setting them up for every domain you own can pose a challenge, especially if your company controls many domains and subdomains. If you are using Gmail, you are in luck, as the company has put down easy-to-follow instructions on domain key generation and DKIM. In case you are using that, you can also find information on setting up different DNS records with cPanel. Once done, you can also use online tools like DKIMvalidator to verify the end-to-end functionality of your SPF and DKIM configuration.
Despite all the resources and tools available today, configuring the framework requires solid craftsmanship and knowledge because the commands used by these protocols aren't widely used. Their syntax is also not precisely simple.
How Does Email Forensics Investigation Help?
IT managers can take measures like security training, robust email-use policies, mock drills, etc., to mitigate email phishing attacks. They can also implement the highly recommended protocols discussed above. However, the truth is that there is no foolproof way to keep email threats at bay. When disaster strikes, companies usually turn to Security Operations Center teams for resolution.
Security Operations Center teams can take a long time to verify and address a phishing attack as there is a series of steps involved, as follows:
- The employees forward suspected emails to the Security Operations Center team in complete and original form. They need to be trained for this to prevent the addition of new risks.
- The Security Operations Center team analyzes the attachments by uploading them to third-party examination websites. Delivery of results can take a long time.
- The team analyzes the header of each email. It verifies the sender's name, address, links, etc., in the email. Additional steps include SPF check, DKIM check, DMARC check, etc.
- If phishing is suspected, the employees are directed to scan all the mailboxes for suspected emails. Without specialized tools, this step can take a long time, and there is a high chance of error.
The conventional approach to handling a phishing attack is time-consuming and undesirable. An advanced eDiscovery and email investigation software such as Stellar Email Forensic mitigates all these complexities. It makes email investigation simple and fast by laying out all the details in multiple views like Hex, hash values, HTML, RTF, Internet Header, etc. Forensic investigators can also search for suspected emails easily with advanced search options, like Boolean Search and Regular Expression Search. Stellar Email Forensic supports analyzing and examining more than 25 file formats, such as EDB, OST, PST, DBX, NSF, MBOX, OLM, TBB, EML, etc. Furthermore, it supports deleted email recovery across all mail clients, such as Exchange, Office 365, GroupWise Server, Google Mail, Notes, etc.), email backup files, and web-based mailboxes with 100% accuracy. In addition, it is capable of providing MD5 and SHA1 hash values of emails.
SPF, DKIM, and DMARC adoption rates across the globe are improving rapidly as these protocols can greatly enhance email security. However, their proper implementation continues to be a challenge across organizations.










 8 min read
8 min read







