What is Email Spoofing?
Email Spoofing is a type of cyberattack in which a hacker tricks a recipient or group into believing that they have received an email from someone they know or trust. It is a popular tactic among hackers. In email spoofing, the attacker fakes the sender's real identity and pretends to be a trusted individual. As a result, the recipient opens the email (that may contain malicious links, attachments, etc.) and responds to the message (asking to share sensitive data and even wire funds).
Types of Email Spoofing
Majorly there are three main types of email spoofing:
- Display Name Spoofing : The email sender's display name is forged in this type of email spoofing. For example, someone can register a new email account using a fake user name.
- Legitimate Domain Spoofing : In this type of spoofing, a hacker uses a trusted email address and mentions the display name as the spoofed name, which matches the domain name and is in sync with the authorized email address.
- Lookalike Domain Spoofing : The attacker registers and uses a similar domain or looks visually identical to the impersonating domain. For example, dom@in.com looks visually similar to domain.com. This type of spoofing is also known as visual spoofing.
How to Identify a Spoofed Email?
As mentioned, in email spoofing, the sender forges the email header fields, so the message appears to be received from a trusted source. Let us look at various fields of an email header to understand and identify a spoofed email. We have taken a sample email header (see Figure 1).
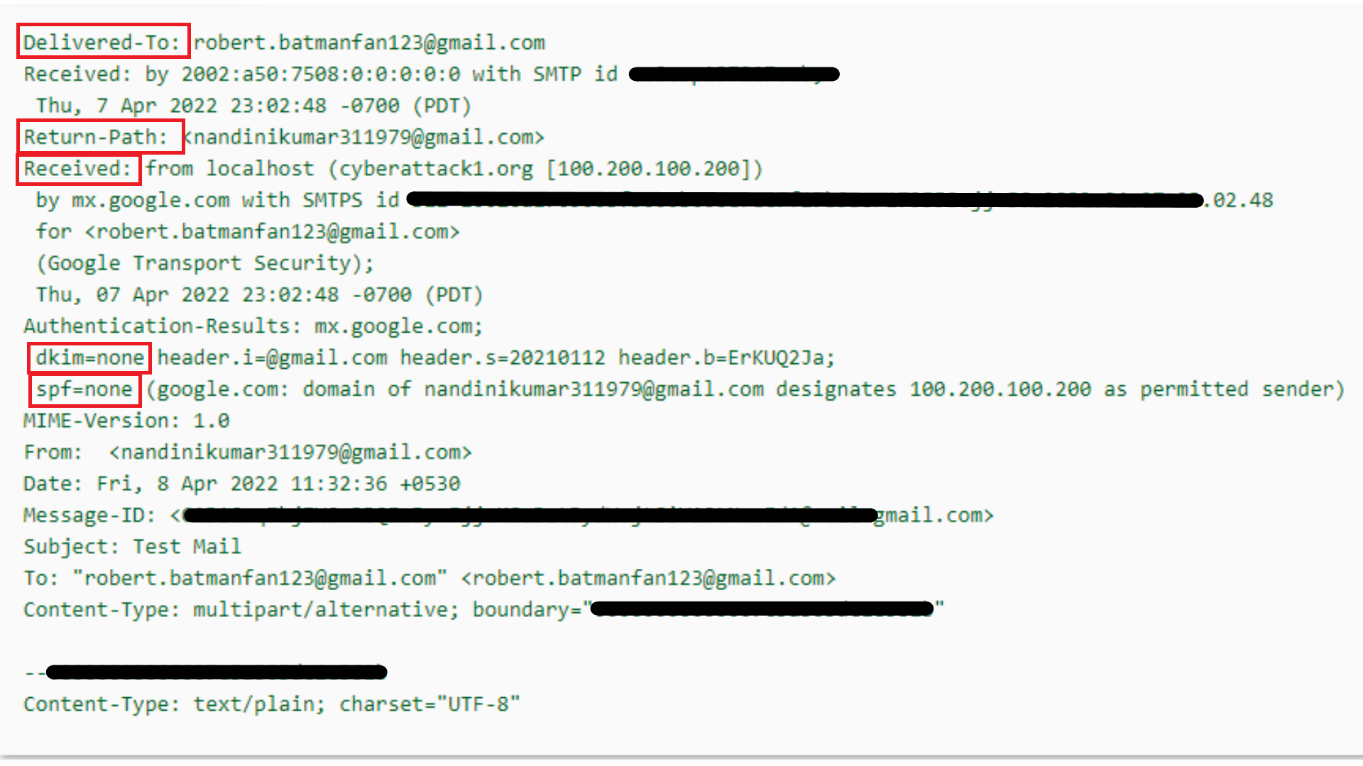
Figure 1: Sample Email Header
In the email header, the Delivered-To field highlights the receiver’s email address. If it is a legitimate email, Return-Path, Received, and From fields will contain the same email address.
As shown in Figure 1, the Received field shows that the email came from the domain cyberattack1.org. Also, the Return-Path and From fields contain the email address nandinikumar311979@gmail.com, which is different from the Received field. This indicates that the header fields have been forged.
How to stop Email Spoofing?
Here are some measures you can follow to prevent email spoofing:
- Monitor email traffic and regularly scan the mail servers : Emails are stored on a mail server. Monitoring the emails and events associated with them can help prevent email spoofing. Forensic examination of Emails can be done effectively and quickly by using an advanced eDiscovery and email forensics software, such as Stellar Email Forensic. It is an advanced software for email search, which helps examine email details in multiple email views, like, Hex, hash values, HTML, RTF, Internet Header, etc. The investigators can also look for suspicious emails with the help of advanced search options, like Boolean search and regular expression search. Furthermore, investigating reports can be exported to multiple, legally acceptable file formats, such as PST, MSG, HTML, PDF, EML, etc.
- Use of anti-malware software: An anti-malware software helps detect and filter spoofed messages. Malware is a computer program usually transmitted via emails as an attachment. Once you open the attachment, the malware gets downloaded into the computer system. As a result, it may damage and manipulate files, resources, and network configurations to a greater extent.
- Implement email security protocols such as SPF, DKIM, and DMARC : To maintain email security, all the three building blocks of protocol-based security, i.e., SPF, DKIM and DMARC, must work together. SPF stands for Sender Policy Framework, which defines which mail servers are authorized to send emails on behalf of the sender. DKIM (Domain Keys Identified Mail) attaches digital signatures to the sender’s messages for authentication purposes, whereas DMARC (Domain-based Message Authentication, Reporting, and Conformance) ensures SPF and DKIM work together. In addition to this, DMARC offers a reporting feature as well.
- Train employees to maintain good cyber hygiene : Cyber hygiene, also called cybersecurity hygiene, is a collection of measures followed by organizations and their employees to maintain the security of their users, their devices, associated networks, and the organization’s data. A user should always inspect the links carefully, which are mentioned in the emails, and never click on the links that seem malicious. Always type the desired URL in the web browser and directly authenticate the official website. Mark those emails as spam and delete them from the inbox that promise riches or create a sense of urgency or danger. One of the good practices while maintaining good cyber hygiene is to have a strong and complex email password, which is difficult to guess. Users should also check email headers closely, especially when someone asks them to click on a link.
- Be extra careful while giving out personal information : Business Email Compromise (BEC), also known as CEO fraud, is a type of cybersecurity attack in which the hacker poses as someone the receiver trusts, usually a boss or a vendor. Some of the most expensive cyberattacks, including some of the Business Email Compromise spoofing attacks, have cost billions of dollars to the organizations. The attacker may ask the recipient to transfer huge amounts, divert payroll, or change bank account details.










 8 min read
8 min read







